-
Pytanie z
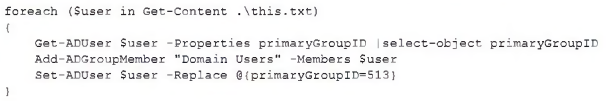
A security analyst recently joined the team and is trying to determine which scripting language is being used in a production script to determine if it is malicious. Given the following script: [photo] Which of the following scripting languages was used in the script?

-
A. PowerShell
-
B. Ruby
-
C. Python
-
D. Shell script
Correct Wrong
-
-
Pytanie z
An incident response team receives an alert to start an investigation of an internet outage. The outage is preventing all users in multiple locations from accessing external SaaS resources. The team determines the organization was impacted by a DDoS attack. Which of the following logs should the team review first?
-
A. CDN
-
B. Vulnerability scanner
-
C. DNS
-
D. Web server
Correct Wrong
In the case of an internet outage caused by a Distributed Denial of Service (DDoS) attack that is preventing users from accessing external SaaS resources, the incident response team should review the DNS (Domain Name System) logs first. C. DNS Explanation: DNS Logs: DDoS attacks often involve overwhelming the DNS infrastructure to disrupt normal internet services. By reviewing DNS logs, the incident response team can identify abnormal traffic patterns, unusual queries, and potential signs of a DDoS attack targeting the organization's DNS servers. Analyzing DNS logs can help pinpoint the attack source, the type of attack, and the affected domains.
-
-
Pytanie z
Which of the following will most likely ensure that mission-critical services are available in the event of an incident?
-
A. Business continuity plan
-
B. Vulnerability management plan
-
C. Disaster recovery plan
-
D. Asset management plan
Correct Wrong
The Answer here is A, because a business continuity plan (BCP) is a document that consists of the critical information an organization needs to continue operating during an unplanned event. The BCP states the essential functions of the business, identifies which systems and processes must be sustained, and details how to maintain them. Note that a Disaster recovery plan is a document to re-energise systems or repair a system after it has been affected by a bad incidents
-
-
Pytanie z
The Chief Information Security Officer wants to eliminate and reduce shadow IT in the enterprise. Several high-risk cloud applications are used that increase the risk to the organization. Which of the following solutions will assist in reducing the risk?
-
A. Deploy a CASB and enable policy enforcement
-
B. Configure MFA with strict access
-
C. Deploy an API gateway
-
D. Enable SSO to the cloud applications
Correct Wrong
-
-
Pytanie z
A SOC manager receives a phone call from an upset customer from Boat. The customer received a vulnerability report two hours ago: but the report did not have a follow-up remediation response from an analyst. Which of the following documents should the SOC manager review to ensure the team is meeting the appropriate contractual obligations for the customer?
-
A. MOU
-
B. SLA
-
C. NDA
-
D. Limitation of liability
Correct Wrong
-
-
Pytanie z
A remote user has received a text message with a link to login and confirm their upcoming work schedule. Which of the following would BEST describe this attack?
-
A. Brute force
-
B. Watering hole
-
C. Typosquatting
-
D. Smishing
Correct Wrong
The Answer: D. Smishing Smishing, or SMS (Short Message Service) phishing, is a social engineering attack that asks for sensitive information using SMS or text messages. The incorrect answers: A. Brute force A brute force attack tries multiple password combinations in an effort to identify the correct authentication details. B. Watering hole A watering hole attack will infect a third-party site visited by the victim. Watering hole attacks are not commonly associated with received text messages. C. Typosquatting Typosquatting uses a misspelling of a domain name to convince victims they are visiting a legitimate website. The information provided in this question does not provide any specific domain names or links.
-
-
Pytanie z
A security administrator needs to block users from visiting websites hosting malicious software. Which of the following would be the BEST way to control this access?
-
A. Honeynet
-
B. Data masking
-
C. DNS filtering
-
D. Data loss prevention
Correct Wrong
The Answer: C. DNS filtering DNS filtering uses a database of known malicious websites to resolve an incorrect or null IP address. If a user attempts to visit a known malicious site, the DNS resolution will fail and the user will not be able to visit the website. The incorrect answers: A. Honeynet A honeynet is a non-production network created to attract attackers. A honeynet is not used to block traffic to known malicious Internet sites. B. Data masking Data masking provides a way to hide data by substitution, shuffling, encryption, and other methods. Data masking does not provide a method of blocking communication to malicious websites. D. Data loss prevention Data Loss Prevention (DLP) systems can identify and block private information from being transferred between systems. DLP does not provide any direct method of blocking network traffic to known malware repositories.
-
-
Pytanie z
Which of the following describes two-factor authentication?
-
A. A printer uses a password and a PIN
-
B. The door to a building requires a fingerprint scan
-
C. An application requires a pseudo-random code
-
D. A Windows Domain requires a password and smart card
Correct Wrong
The Answer: D. A Windows Domain requires a password and smart card The multiple factors of authentication for this Windows Domain are a password (something you know), and a smart card (something you have). The incorrect answers: A. A printer uses a password and a PIN A password and a PIN (Personal Identification Number) are both something you know, so only one authentication factor is used. B. The door to a building requires a fingerprint scan A biometric scan (something you are) is a single factor of authentication. C. An application requires a pseudo-random code Pseudo-random authentication codes are often provided using a hardware dongle or mobile app. This single factor of authentication is something you have.
-
-
Pytanie z
A Linux administrator is downloading an updated version of her Linux distribution. The download site shows a link to the ISO and a SHA256 hash value. Which of these would describe the use of this hash value?
-
A. Verifies that the file was not corrupted during the file transfer
-
B. Provides a key for decrypting the ISO after download
-
C. Authenticates the site as an official ISO distribution site
-
D. Confirms that the file does not contain any malware
Correct Wrong
The Answer: A. Verifies that the file was not corrupted during the file transfer Once the file is downloaded, the administrator can calculate the file’s SHA256 hash and confirm that it matches the value on the website. The incorrect answers: B. Provides a key for decrypting the ISO after download ISO files containing public information are usually distributed without any encryption, and a hash value would not commonly be used as a decryption key. C. Authenticates the site as an official ISO distribution site Although it’s important to download files from known good sites, providing a hash value on a site would not provide any information about the site’s authentication. D. Confirms that the file does not contain any malware A hash value doesn’t inherently provide any protection against malware.
-
-
Pytanie z
An organization is implementing a security model where all application requests must be validated at a policy enforcement point. Which of the following would BEST describe this model?
-
A. Public key infrastructure
-
B. Zero trust
-
C. Discretionary access control
-
D. Federation
Correct Wrong
The Answer: B. Zero trust Zero trust describes a model where nothing is inherently trusted and everything must be verified to gain access. A central policy enforcement point is commonly used to implement a zero trust architecture. The incorrect answers: A. Public key infrastructure A public key infrastructure (PKI) uses public and private keys to provide confidentiality and integrity. Asymmetric encryption and digital signatures are used as foundational technologies in PKI. C. Discretionary access control. Discretionary access control is an authorization method where the owner of the data determines the scope and type of access. A discretionary access control model does not specifically define how the authorization is implemented. D. Federation Federation provides a way to manage authentication to a third-party database.
-
-
Pytanie z
A corporate security team would like to consolidate and protect the private keys across all of their web servers. Which of these would be the BEST way to securely store these keys?
-
A. Integrate an HSM
-
B. Implement full disk encryption on the web servers
-
C. Use a TPM
-
D. Upgrade the web servers to use a UEFI BIOS
Correct Wrong
The Answer: A. Integrate an HSM An HSM (Hardware Security Module) is a high-end cryptographic hardware appliance that can securely store keys and certificates for all devices. The incorrect answers: B. Implement full disk encryption on the web servers Full-disk encryption would only protect the keys if someone does not have the proper credentials, and it won’t help consolidate all of the web server keys to a central point. C. Use a TPM A TPM (Trusted Platform Module) is used on individual devices to provide cryptographic functions and securely store encryption keys. Individual TPMs would not provide any consolidation of web server private keys. D. Upgrade the web servers to use a UEFI BIOS A UEFI (Unified Extensible Firmware Interface) BIOS (Basic Input/ Output System) does not provide
-
-
Pytanie z
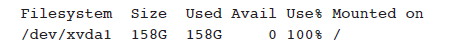
A Linux administrator has received a ticket complaining of response issues with a database server. After connecting to the server, the administrator views this information: [photo] Which of the following would BEST describe this information?

-
A. Buffer overflow
-
B. Resource consumption
-
C. SQL injection
-
D. Race condition
Correct Wrong
The Answer: B. Resource consumption The available storage on the local filesystem has been depleted, and the information shows 0 bytes available. More drive space would need to be available for the server to return to normal response times. The incorrect answers: A. Buffer overflow A buffer overflow allows an attacker to manipulate the contents of memory. A filesystem at 100% utilization does not describe the contents in memory. C. SQL injection A SQL injection is a network attack type used to access database information directly. A SQL injection would not cause significant storage drive utilization. D. Race condition A race condition is a programming issue where a portion of the application is making changes not seen by other parts of the application. A race condition does not commonly use all available storage space on the device.
-
-
Pytanie z
A security administrator receives a report each week showing a Linux vulnerability associated with a Windows server. Which of the following would prevent this information from appearing in the report?
-
A. Alert tuning
-
B. Application benchmarking
-
C. SIEM aggregation
-
D. Data archiving
Correct Wrong
The Answer: A. Alert tuning Our monitoring systems are not always perfect, and many require ongoing tuning to properly configure alerts and notifications of important events. The incorrect answers: B. Application benchmarking Creating an application benchmark can help with the planning and implementation of security monitoring. However, the creation of an application benchmark does not change the alert messages created by a third-party monitoring system. C. SIEM aggregation A SIEM (Security Information and Event Manager) can be used to aggregate all log files to a centralized reporting system. Creating a centralized log repository does not remove invalid alerts from a weekly report. D. Data archiving Many organizations are required to archive data for long-term security monitoring. Simply archiving the data does not change the alert notification in a weekly report.
-
-
Pytanie z
A company is installing access points in all of their remote sites. Which of the following would provide confidentiality for all wireless data?
-
A. 802.1X
-
B. WPA3
-
C. RADIUS
-
D. MDM
Correct Wrong
The Answer: B. WPA3 WPA3 (Wi-Fi Protected Access 3) is an encryption protocol used on wireless networks. All data sent over a WPA3-protected wireless network will be encrypted. The incorrect answers: A. 802.1X 802.1X is a standard for authentication using AAA (Authentication, Authorization and Accounting) services. 802.1X is commonly used in conjunction with LDAP, RADIUS, or similar authentication services. C. RADIUS RADIUS (Remote Authentication Dial-In User Service) is an authentication protocol used for centralized authentication. RADIUS is commonly used in conjunction with 802.1X, but RADIUS does not provide data confidentiality or encryption. D. MDM An MDM (Mobile Device Manager) is used to manage and control an organization's mobile phones and tablets. MDM policies are not used to manage the confidentiality settings of a wireless access point.
-
-
Pytanie z
A company has identified a compromised server, and the security team would like to know if an attacker has used this device to move between systems. Which of the following would be the BEST way to provide this information?
-
A. DNS server logs
-
B. Penetration test
-
C. NetFlow logs
-
D. Email metadata
Correct Wrong
The Answer: C. NetFlow logs NetFlow information can provide a summary of network traffic, application usage, and details of network conversations. The NetFlow logs will show all conversations from this device to any others in the network. The incorrect answers: A. DNS server logs DNS server logs will document all name resolutions, but an attacker may not be using a DNS server and may prefer accessing devices by IP address. B. Penetration test A penetration test may identify any vulnerabilities that exist on the server, but it won't provide any information about traffic flows or connections initiated by an attacker. D. Email metadata An email header contains the IP addresses of email servers used to transfer the message, and security signatures to verify the sender. The metadata in an email header would not contain information on traffic flows associated with this attacker.
-
-
Pytanie z
A system administrator has protected a set of system backups with an encryption key. The system administrator used the same key when restoring files from this backup. Which of the following would BEST describe this encryption type?
-
A. Asymmetric
-
B. Key escrow
-
C. Symmetric
-
D. Out-of-band key exchange
Correct Wrong
-
-
Pytanie z
A security administrator is reviewing a report showing a number of devices on internal networks are connecting with servers in the data center network. Which of the following security systems should be added to prevent internal systems from accessing data center devices?
-
A. VPN
-
B. IPS
-
C. SIEM
-
D. ACL
Correct Wrong
The Answer: D. ACL An ACL (Access Control List) is a security control commonly implemented on routers to allow or restrict traffic flows through the network. The incorrect answers: A. VPN A VPN (Virtual Private Network) can be used to secure data traversing the network, but it’s not commonly used to control traffic flows on an internal network. B. IPS An IPS (Intrusion Prevention System) is designed to identify and block known vulnerabilities traversing the network. An IPS is not used to control other traffic flows. C. SIEM A SIEM (Security Information and Event Management) server is commonly used to consolidate and report on log files. A SIEM would not be able to control or limit network communication.
-
-
Pytanie z
A user in the mail room has reported an overall slowdown of his shipping management software. An anti-virus scan did not identify any issues, but a more thorough malware scan identified a kernel driver which is not part of the original operating system installation. Which of the following malware was installed on this system?
-
A. Rootkit
-
B. Logic bomb
-
C. Bloatware
-
D. Ransomware
Correct Wrong
The Answer: A. Rootkit A rootkit often modifies core system files and becomes effectively invisible to the rest of the operating system. The modification of system files and specialized kernel-level drivers are common rootkit techniques. The incorrect answers: B. Logic bomb A logic bomb waits for a predefined event, and then executes at that event time. This event may be a time of day, a user event, or any other identifiable event. C. Bloatware Bloatware consists of apps which have been preinstalled onto new phones, tablets, or computers. Some of these apps can create resource contention for CPU time, memory capacity, or free storage space. D. Ransomware Ransomware makes itself quite visible on your system, and it usually presents warning messages and information on how to remove the ransomware from the system. E. Keylogger A keylogger captures keyboard and mouse input and sends that information to another device. This usually means the keylogger has a visible component in the list of processes, and the keylogger traffic can often be seen on the network.
-
-
Pytanie z
A security administrator has discovered an employee exfiltrating confidential company information by embedding data within image files and emailing the images to a third-party. Which of the following would best describe this activity?
-
A. Digital signatures
-
B. Steganography
-
C. Salting
-
D. Data masking
Correct Wrong
The Answer: B. Steganography Steganography is the process of hiding information within another document. For example, one common method of steganography embeds data or documents within image files. The incorrect answers: A. Digital signatures A digital signature is a cryptographic method used to check the integrity, authentication, and non-repudiation of a message. Digital signatures are not used to hide information within image files. C. Salting Salting adds information the hashing process to ensure a unique hash value. The salting process does not involve embedding or hiding data within other types of media. D. Data masking Data masking replaces the display of sensitive information with another value. Replacing a credit card number on a receipt with a series of asterisks would be an example of data masking.
-
-
Pytanie z
A security administrator is installing a web server with a newly built operating system. Which of the following would be the best way to harden this OS?
-
A. Create a backup schedule
-
B. Install a device certificate
-
C. Remove unnecessary software
-
D. Disable power management features
Correct Wrong
The Answer: C. Remove unnecessary software The process of hardening an operating system makes it more difficult to attack. In this example, the only step that would limit the attack surface is to remove any unnecessary or unused software. The incorrect answers: A. Create a backup schedule Although a backup schedule is an important security task, the process of performing backups doesn't make the system any more resistant to a potential attack. B. Install a device certificate A device certificate can be used to verify the ownership of a remote system. However, installing a device certificate does not make the remote system more resistant to an attack. D. Disable power management features Disabling the power management features of an operating system does not generally have any impact on the overall security of the system.
-
-
Pytanie z
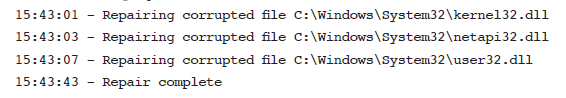
A system administrator is viewing this output from a file integrity monitoring report: [photo] Which of the following malware types is the MOST likely cause of this output?

-
A. Ransomware
-
B. Logic bomb
-
C. Rootkit
-
D. Keylogger
Correct Wrong
The Answer: C. Rootkit A rootkit modifies operating system files to become part of the core OS. The kernel, user, and networking libraries in Windows are core operating system files. The incorrect answers: A. Ransomware Ransomware commonly presents itself as a warning message on the user's screen, and most aspects of the operating system would be disabled. Ransomware also encrypts user documents and would not easily be repaired by replacing system files. B. Logic bomb A logic bomb waits for a predefined event to begin operation. Logic bombs do not commonly modify core operating system files. D. Keylogger A keylogger does not commonly embed itself in core operating system files. Keyloggers often run as an independent process and compile logs and keystrokes to send across the network to the attacker.
-
-
Pytanie z
A security administrator is implementing an authentication system for the company. Which of the following would be the best choice for validating login credentials for all usernames and passwords in the authentication system?
-
A. CA
-
B. SIEM
-
C. LDAP
-
D. WAF
Correct Wrong
The Answer: C. LDAP LDAP (Lightweight Directory Access Protocol) is a common standard for authentication. LDAP is an open standard and is available across many different operating systems and devices. The incorrect answers: A. CA A CA (Certificate Authority) is a trusted service for certificate creation and management. The CA itself is not responsible for validating login credentials. B. SIEM A SIEM (Security and Information Management) service consolidates log files from diverse systems and can create reports based on the correlation of this data. A SIEM is not part of the authentication process. D. WAF A WAF (Web Application Firewall) is used to protect a web-based application from
-
-
Pytanie z
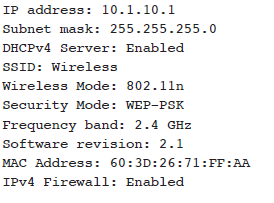
An access point in a corporate headquarters office has the following configuration: [photo] Which of the following would apply to this configuration?

-
A. Invalid frequency band
-
B. Weak encryption
-
C. Incorrect IP address and subnet mask
-
D. Invalid software version
Correct Wrong
The Answer: B. Weak encryption A common issue is weak or outdated security configurations. Older encryptions such as DES and WEP should be updated to use newer and stronger encryption technologies. The incorrect answers: A. Invalid frequency band The 2.4 GHz frequency band is a valid frequency range for 802.11n networks. C. Incorrect IP address and subnet mask None of the listed configuration settings show any issues with the IP address or subnet mask. D. Invalid software version The software version of the access point does not have any configuration options and would not be considered invalid.
-
-
Pytanie z
A system administrator would like to prove an email message was sent by a specific person. Which of the following describes the verification of this message source?
-
A. Non-repudiation
-
B. Key escrow
-
C. Asymmetric encryption
-
D. Steganography
Correct Wrong
The Answer: A. Non-repudiation Non-repudiation is used to verify the source of data or a message. Digital signatures are commonly used for non-repudiation. The incorrect answers: B. Key escrow Key escrow describes a third-party responsible for holding or managing keys or certificates. Key escrow does not provide verification of a data source. C. Asymmetric encryption Asymmetric encryption describes data encryption using one key and the decryption of this data with a different key. The use of asymmetric encryption by itself does not provide proof of origin. D. Steganography Steganography describes hiding one type of data within another media type. For example, hiding encrypted data within an image is a form of steganography. Steganography does not provide proof of origin.
-
-
Pytanie z
A security administrator would like to monitor all outbound Internet connections for malicious software. Which of the following would provide this functionality?
-
A. Jump server
-
B. IPsec tunnel
-
C. Forward proxy
-
D. Load balancer
Correct Wrong
The Answer: C. Forward proxy A proxy server can be used to monitor incoming and outgoing network communication. Proxy servers can be used to identify malicious software, filter content, or increase performance through file caching. The incorrect answers: A. Jump server A jump server is commonly used to provide administrative access to a secure network connection. Jump servers are not used to monitor or filter Internet connections. B. IPsec tunnel An IPsec tunnel is associated with an encrypted connection between devices or sites. An IPsec tunnel would not be used to monitor or manage network content or Internet connections. D. Load balancer Load balancers are used to increase capacity by separating the processing load between multiple servers. Load balancers are not used for network monitoring or security filtering.
-


GIPHY App Key not set. Please check settings