-
Pytanie z
A security engineer needs to build a solution to satisfy regulatory requirements that stale certain critical servers must be accessed using MFA However, the critical servers are older and are unable to support the addition of MFA, Which of te following will the engineer MOST likely use to achieve this objective?
-
A. A forward proxy
-
B. A stateful firewall
-
C. A jump server
-
D. A port tap
Correct Wrong
A jump server is a secure host that allows users to access other servers within a network. The jump server acts as an intermediary, and users can access other servers via the jump server after authenticating with MFA
-
-
Pytanie z
After a phishing scam fora user’s credentials, the red team was able to craft payload to deploy on a server. The attack allowed the installation of malicious software that initiates a new remote session. Which of the following types of attacks has occurred?
-
A. Privilege escalation
-
B. Session replay
-
C. Application programming interface
-
D. Directory traversal
Correct Wrong
"Privilege escalation is the act of exploiting a bug, design flaw, or configuration oversight in an operating system or software application to gain elevated access to resources that are normally protected from an application or user." In this scenario, the red team was able to install malicious software, which would require elevated privileges to access and install. Therefore, the type of attack that occurred is privilege escalation. References: CompTIA Security+ Study Guide, pages 111-112
-
-
Pytanie z
Which of the following BEST describes a social-engineering attack that relies on an executive at a small business visiting a fake banking website where credit card and account details are harvested?
-
A. Whaling
-
B. Spam
-
C. Invoice scam
-
D. Pharming
Correct Wrong
Whaling is a type of phishing attack that targets high-profile individuals, such as executives, to steal sensitive information or gain access to their accounts.
-
-
Pytanie z
A security analyst is responding to an alert from the SIEM. The alert states that malware was discovered on a host and was not automatically deleted. Which of the following would be BEST for the analyst to perform?
-
A. Add a deny-all rule to that host in the network ACL
-
B. Implement a network-wide scan for other instances of the malware
-
C. Quarantine the host from other parts of the network
-
D. Revoke the client’s network access certificates
Correct Wrong
When malware is discovered on a host, the best course of action is to quarantine the host from other parts of the network. This prevents the malware from spreading and potentially infecting other hosts. Adding a deny-all rule to the host in the network ACL may prevent legitimate traffic from being processed, implementing a network-wide scan is time-consuming and may not be necessary, and revoking the client's network access certificates is an extreme measure that may not be warranted. References: CompTIA Security+ Study Guide, pages 113-114
-
-
Pytanie z
A company’s public-facing website, https://www.organization.com, has an IP address of 166.18.75.6. However, over the past hour the SOC has received reports of the site’s homepage displaying incorrect information. A quick nslookup search shows hitps://;www.organization.com is pointing to 151.191.122.115. Which of the following is occurring?
-
A. DoS attack
-
B. ARP poisoning
-
C. DNS spoofing
-
D. NXDOMAIN attack
Correct Wrong
The issue is DNS spoofing, where the DNS resolution has been compromised and is pointing to a malicious IP address. References: CompTIA Security+ Study Guide: Exam SY0-601, Chapter 7
-
-
Pytanie z
A company recently decided to allow its employees to use their personally owned devices for tasks like checking email and messaging via mobile applications. The company would like to use MDM, but employees are concerned about the loss of personal data. Which of the following should the IT department implement to BEST protect the company against company data loss while still addressing the employees’ concerns?
-
A. Enable the remote-wiping option in the MDM software in case the phone is stolen.
-
B. Configure the MDM software to enforce the use of PINs to access the phone.
-
C. Configure MDM for FDE without enabling the lock screen.
-
D. Perform a factory reset on the phone before installing the company’s applications.
Correct Wrong
MDM software is a type of remote asset-management software that runs from a central server. It is used by businesses to optimize the functionality and security of their mobile devices, including smartphones and tablets. It can monitor and regulate both corporate-owned and personally owned devices to the organization’s policies. FDE stands for full disk encryption, which is a method of encrypting all data on a device’s storage. FDE can protect data from unauthorized access in case the device is lost or stolen. If a company decides to allow its employees to use their personally owned devices for work tasks, it should configure MDM software to enforce FDE on those devices. This way, the company can protect its data from being exposed if the device falls into the wrong hands. However, employees may be concerned about the loss of personal data if the company also enables the remote-wiping option in the MDM software. Remote wiping is a feature that allows the company to erase all data on a device remotely in case of theft or loss. Remote wiping can also affect personal data on the device, which may not be acceptable to employees. Therefore, a possible compromise is to configure MDM for FDE without enabling the lock screen. This means that the device will be encrypted, but it will not require a password or PIN to unlock it. This way, employees can access their personal data easily, while the company can still protect its data with encryption. The other options are not correct because: A. Enable the remote-wiping option in the MDM software in case the phone is stolen. This option may address the company’s concern about data loss, but it may not address the employees’ concern about personal data loss. Remote wiping can erase both work and personal data on the device, which may not be desirable for employees. B. Configure the MDM software to enforce the use of PINs to access the phone. This option may enhance the security of the device, but it may not address the company’s concern about data loss. PINs can be guessed or bypassed by attackers, and they do not protect data if the device is physically accessed. D. Perform a factory reset on the phone before installing the company’s applications. This option may address the company’s concern about data loss, but it may not address the employees’ concern about personal data loss. A factory reset will erase all data on the device, including personal data, which may not be acceptable to employees. According to CompTIA Security+ SY0-601 Exam Objectives 2.4 Given a scenario, implement secure systems design: “MDM software is a type of remote asset-management software that runs from a central server1. It is used by businesses to optimize the functionality and security of their mobile devices, including smartphones and tablets2.” “FDE stands for full disk encryption, which is a method of encrypting all data on a device’s storage3.” References: https://www.comptia.org/certifications/security#examdetails https://www.comptia.org/content/guides/comptia-security-sy0-601-exam-objectives https://www.makeuseof.com/what-is-mobile-device-management-mdm-software/
-
-
Pytanie z
A company Is planning to install a guest wireless network so visitors will be able to access the Internet. The stakeholders want the network to be easy to connect to so time is not wasted during meetings. The WAPs are configured so that power levels and antennas cover only the conference rooms where visitors will attend meetings. Which of the following would BEST protect the company’s Internal wireless network against visitors accessing company resources?
-
A. Configure the guest wireless network to be on a separate VLAN from the company’s internal wireless network
-
B. Change the password for the guest wireless network every month.
-
C. Decrease the power levels of the access points for the guest wireless network.
-
D. Enable WPA2 using 802.1X for logging on to the guest wireless network.
Correct Wrong
Configuring the guest wireless network on a separate VLAN from the company's internal wireless network will prevent visitors from accessing company resources. References: CompTIA Security+ Study Guide: Exam SY0-601, Chapter 4
-
-
Pytanie z
Which of the following biometric authentication methods is the MOST accurate?
-
A. Gait
-
B. Retina
-
C. Signature
-
D. Voice
Correct Wrong
Retina authentication is the most accurate biometric authentication method. Retina authentication is based on recognizing the unique pattern of blood vessels and other features in the retina. This makes it virtually impossible to duplicate or bypass, making it the most secure form of biometric authentication currently available.
-
-
Pytanie z
As part of the building process for a web application, the compliance team requires that all PKI certificates are rotated annually and can only contain wildcards at the secondary subdomain level. Which of the following certificate properties will meet these requirements?
-
A. HTTPS://*.comptia.org, Valid from April 10 00:00:00 2021 – April 8 12:00:00 2022
-
B. HTTPS://app1.comptia.org, Valid from April 10 00:00:00 2021 – April 8 12:00:00 2022
-
C. HTTPS://*.app1.comptia.org, Valid from April 10 00:00:00 2021 – April 8 12:00:00 2022
-
D. HTTPS://*.comptia.org, Valid from April 10 00:00:00 2021 – April 8 12:00:00 2023
Correct Wrong
PKI certificates are digital certificates that use public key infrastructure (PKI) to verify the identity and authenticity of a sender and a receiver of data1. PKI certificates can be used to secure web applications with HTTPS, which is a protocol that encrypts and protects the data transmitted over the internet1. One of the properties of PKI certificates is the domain name, which is the name of the website or web application that the certificate is issued for2. The domain name can be either a specific name, such as app1.comptia.org, or a wildcard name, such as *.comptia.org2. A wildcard name means that the certificate can be used with multiple subdomains of a domain, such as payment.comptia.org or contact.comptia.org2. Another property of PKI certificates is the validity period, which is the time span during which the certificate is valid and can be used3. The validity period is determined by the certificate authority (CA) that issues the certificate, and it usually ranges from one to three years3. The validity period can be checked by looking at the valid from and valid to dates on the certificate3. Based on these properties, the certificate that will meet the requirements of rotating annually and only containing wildcards at the secondary subdomain level is A. HTTPS://*.comptia.org, Valid from April 10 00:00:00 2021 - April 8 12:00:00 2022. This certificate has a wildcard character (*) at the secondary subdomain level, which means it can be used with any subdomain of comptia.org2. It also has a validity period of one year, which means it needs to be rotated annually3.
-
-
Pytanie z
A desktop support technician recently installed a new document-scanning software program on a computer. However, when the end user tried to launch the program, it did not respond. Which of the following is MOST likely the cause?
-
A. A new firewall rule is needed to access the application.
-
B. The system was quarantined for missing software updates.
-
C. The software was not added to the application whitelist.
-
D. The system was isolated from the network due to infected software
Correct Wrong
The most likely cause of the document-scanning software program not responding when launched by the end user is that the software was not added to the application whitelist. An application whitelist is a list of approved software applications that are allowed to run on a system. If the software is not on the whitelist, it may be blocked from running by the system's security policies. Adding the software to the whitelist should resolve the issue and allow the program to run. References: https://www.techopedia.com/definition/31541/application-whitelisting
-
-
Pytanie z
A large enterprise has moved all its data to the cloud behind strong authentication and encryption. A sales director recently had a laptop stolen, and later, enterprise data was found to have been compromised from a local database. Which of the following was the MOST likely cause?
-
A. Shadow IT
-
B. Credential stuffing
-
C. SQL injection
-
D. Man in the browser
-
E. Bluejacking
Correct Wrong
The most likely cause of the enterprise data being compromised from a local database is Shadow IT. Shadow IT is the use of unauthorized applications or devices by employees to access company resources. In this case, the sales director's laptop was stolen, and the attacker was able to use it to access the local database, which was not secured properly, allowing unauthorized access to sensitive data. References: CompTIA Security+ Certification Exam Objectives - Exam SY0-601
-
-
Pytanie z
After a WiFi scan of a local office was conducted, an unknown wireless signal was identified Upon investigation, an unknown Raspberry Pi device was found connected to an Ethernet port using a single connection. Which of the following BEST describes the purpose of this device?
-
A. loT sensor
-
B. Evil twin
-
C. Rogue access point
-
D. On-path attack
Correct Wrong
A Raspberry Pi device connected to an Ethernet port could be configured as a rogue access point, allowing an attacker to intercept and analyze network traffic or perform other malicious activities. References: CompTIA Security+ SY0-601 Exam Objectives: 3.2 Given a scenario, implement secure network architecture concepts.
-
-
Pytanie z
A third party asked a user to share a public key for secure communication. Which of the following file formats should the user choose to share the key?
-
A. .pfx
-
B. .csr
-
C. .pvk
-
D. .cer
Correct Wrong
A user should choose the .cer file format to share a public key for secure communication. A .cer file is a public key certificate that can be shared with third parties to enable secure communication. References: CompTIA Security+ Study Guide, Exam SY0-601, 4th Edition, Chapter 6: Cryptography, pp. 301-302. A public key is a cryptographic key that can be used to encrypt or verify data. A public key file is a file that contains one or more public keys in a specific format. There are different formats for public key files, depending on the application and the algorithm used. Some of the common formats are: .pfx: This is a file format that stores a certificate and its private and public keys. It is also known as PKCS#12 or Personal Information Exchange. It is used by some applications such as Microsoft Internet Explorer and Outlook to import and export certificates and keys.1 .csr: This is a file format that stores a Certificate Signing Request, which is a message sent to a Certificate Authority (CA) to request a digital certificate. It contains the public key and some information about the identity of the requester. It is also known as PKCS#10 or Certification Request Syntax.2 .pvk: This is a file format that stores a private key for Microsoft Authenticode code signing. It is used with a .spc file that contains the certificate and public key.3 .cer: This is a file format that stores a certificate, which is a document that binds a public key to an identity. It is also known as DER or Distinguished Encoding Rules. It is used by some applications such as OpenSSL and Java to read and write certificates.4
-
-
Pytanie z
Which of the following authentication methods is considered to be the LEAST secure?
-
A. TOTP
-
B. SMS
-
C. HOTP
-
D. Token key
Correct Wrong
-
-
Pytanie z
A security administrator is working on a solution to protect passwords stored in a database against rainbow table attacks Which of the following should the administrator consider?
-
A. Hashing
-
B. Salting
-
C. Lightweight cryptography
-
D. Steganography
Correct Wrong
Salting is a technique that adds random data to a password before hashing it. This makes the hash output more unique and unpredictable, and prevents attackers from using precomputed tables (such as rainbow tables) to crack the password hash. Salting also reduces the risk of collisions, which occur when different passwords produce the same hash. References: https://www.comptia.org/certifications/security#examdetails https://www.comptia.org/content/guides/comptia-security-sy0-601-exam-objectives https://auth0.com/blog/adding-salt-to-hashing-a-better-way-to-store-passwords/
-
-
Pytanie z
The alert indicates an attacker entered thousands of characters into the text box of a web form. The web form was intended for legitimate customers to enter their phone numbers. Which of the attacks has most likely occurred?
-
A. Privilege escalation
-
B. Buffer overflow
-
C. Resource exhaustion
-
D. Cross-site scripting
Correct Wrong
A buffer overflow attack occurs when an attacker inputs more data than the buffer can store, causing the excess data to overwrite adjacent memory locations and corrupt or execute code1. In this case, the attacker entered thousands of characters into a text box that was intended for phone numbers, which are much shorter. This could result in a buffer overflow attack that compromises the web application or server. The other options are not related to this scenario. Privilege escalation is when an attacker gains unauthorized access to higher-level privileges or resources2. Resource exhaustion is when an attacker consumes all the available resources of a system, such as CPU, memory, disk space, etc., to cause a denial of service3. Cross-site scripting is when an attacker injects malicious code into a web page that is executed by the browser of a victim who visits the page. References: 1: https://www.fortinet.com/resources/cyberglossary/buffer-overflow 2: https://www.imperva.com/learn/application-security/privilege-escalation/ 3: https://www.imperva.com/learn/application-security/resource-exhaustion/ : https://owasp.org/www-community/attacks/xss/
-
-
Pytanie z
A company has hired an assessment team to test the security of the corporate network and employee vigilance. Only the Chief Executive Officer and Chief Operating Officer are aware of this exercise, and very little information has been provided to the assessors. Which of the following is taking place?
-
A. A red-team test
-
B. A white-team test
-
C. A purple-team test
-
D. A blue-team test
Correct Wrong
A red-team test is a type of security assessment that simulates a real-world attack on an organization’s network, systems, applications, and people. The goal of a red-team test is to evaluate the organization’s security posture, identify vulnerabilities and gaps, and test the effectiveness of its detection and response capabilities. A red-team test is usually performed by a group of highly skilled security professionals who act as adversaries and use various tools and techniques to breach the organization’s defenses. A red-team test is often conducted without the knowledge or consent of most of the organization’s staff, except for a few senior executives who authorize and oversee the exercise. References: https://www.comptia.org/certifications/security#examdetails https://www.comptia.org/content/guides/comptia-security-sy0-601-exam-objectives https://cybersecurity.att.com/blogs/security-essentials/what-is-red-teaming
-
-
Pytanie z
A retail store has a business requirement to deploy a kiosk computer In an open area The kiosk computer’s operating system has been hardened and tested. A security engineer IS concerned that someone could use removable media to install a rootkit Mich of the should the security engineer configure to BEST protect the kiosk computer?
-
A. Measured boot
-
B. Boot attestation
-
C. UEFI
-
D. EDR
Correct Wrong
Boot attestation is a security feature that enables the computer to verify the integrity of its operating system before it boots. It does this by performing a hash of the operating system and comparing it to the expected hash of the operating system. If the hashes do not match, the computer will not boot and the rootkit will not be allowed to run. This process is also known as measured boot or secure boot. According to the CompTIA Security+ Study Guide, “Secure Boot is a feature of Unified Extensible Firmware Interface (UEFI) that ensures that code that is executed during the boot process has been authenticated by a cryptographic signature. Secure Boot prevents malicious code from running at boot time, thus providing assurance that the system is executing only code that is legitimate. This provides a measure of protection against rootkits and other malicious code that is designed to run at boot time.”
-
-
Pytanie z
A security analyst is reviewing packet capture data from a compromised host On the In the packet capture. analyst locates packets that contain large of text, Which Of following is most likely installed on compromised host?
-
A. Keylogger
-
B. Spyware
-
C. Torjan
-
D. Ransomware
Correct Wrong
A keylogger is a type of malware that records the keystrokes of the user and sends them to a remote attacker. The attacker can use the keystrokes to steal the user’s credentials, personal information, or other sensitive data. A keylogger can generate packets that contain large amounts of text, as the packet capture data shows.
-
-
Pytanie z
Audit logs indicate an administrative account that belongs to a security engineer has been locked out multiple times during the day. The security engineer has been on vacation (or a few days. Which of the following attacks can the account lockout be attributed to?
-
A. Backdoor
-
B. Brute-force
-
C. Rootkit
-
D. Trojan
Correct Wrong
Explanation The account lockout can be attributed to a brute-force attack. A brute-force attack is a type of attack where an attacker attempts to guess a user's password by continually trying different combinations of characters. In this case, it is likely that the security engineer's account was locked out due to an attacker attempting to guess their password. Backdoor, rootkit, and Trojan attacks are not relevant in this scenario.
-
-
Pytanie z
A technician is setting up a new firewall on a network segment to allow web traffic to the internet while hardening the network. After the firewall is configured, users receive errors stating the website could not be located. Which of the following would best correct the issue?
-
A. Setting an explicit deny to all traffic using port 80 instead of 443
-
B. Moving the implicit deny from the bottom of the rule set to the top
-
C. Configuring the first line in the rule set to allow all traffic
-
D. Ensuring that port 53 has been explicitly allowed in the rule set
Correct Wrong
Port 53 is the default port for DNS traffic. If the firewall is blocking port 53, then users will not be able to resolve domain names and will receive errors stating that the website could not be located. The other options would not correct the issue. Setting an explicit deny to all traffic using port 80 instead of 443 would block all HTTP traffic, not just web traffic. Moving the implicit deny from the bottom of the rule set to the top would make the deny rule more restrictive, which would not solve the issue. Configuring the first line in the rule set to allow all traffic would allow all traffic, including malicious traffic, which is not a good security practice. Therefore, the best way to correct the issue is to ensure that port 53 has been explicitly allowed in the rule set. Here are some additional information about DNS traffic: DNS traffic is used to resolve domain names to IP addresses. DNS traffic is typically unencrypted, which makes it vulnerable to eavesdropping. There are a number of ways to secure DNS traffic, such as using DNS over HTTPS (DoH) or DNS over TLS (DoT).
-
-
Pytanie z
A security analyst receives an alert from the company’s S1EM that anomalous activity is coming from a local source IP address of 192 168 34.26 The Chief Information Security Officer asks the analyst to block the originating source Several days later another employee opens an internal ticket stating that vulnerability scans are no longer being performed property. The IP address the employee provides is 192 168.34 26. Which of the following describes this type of alert?
-
A. True positive
-
B. True negative
-
C. False positive
-
D. False negative
Correct Wrong
A false positive is a type of alert that indicates a security incident when there is none. It can be caused by misconfigured or overly sensitive security tools or systems that generate false or irrelevant alerts. In this case, the alert from the company’s SIEM that Mimikatz attempted to run on the remote systems was a false positive because it was triggered by a legitimate vulnerability scanning tool that uses Mimikatz as part of its functionality.
-
-
Pytanie z
To reduce and limit software and infrastructure costs the Chief Information Officer has requested to move email services to the cloud. The cloud provider and the organization must have secunty controls to protect sensitive data Which of the following cloud services would best accommodate the request?

-
A. laaS
-
B. PaaS
-
C. DaaS
-
D. SaaS
Correct Wrong
-
-
Pytanie z
A security analyst is concerned about traffic initiated to the dark web from the corporate LAN. Which of the following networks should the analyst monitor?
-
A. SFTP
-
B. AIS
-
C. Tor
-
D. loC
Correct Wrong
Tor (The Onion Router) is a network and a software that enables anonymous communication over the internet. It routes the traffic through multiple relays and encrypts it at each layer, making it difficult to trace or monitor. It can access the dark web, which is a part of the internet that is hidden from conventional search engines and requires special software or configurations to access
-
-
Pytanie z
A user downloaded an extension for a browser, and the user’s device later became infected. The analyst who Is Investigating the Incident saw various logs where the attacker was hiding activity by deleting data. The following was observed running:
New-Partition -DiskNumber 2 -UseMaximumSize -AssignDriveLetter C| Format-Volume -Driveletter C – FileSystemLabel „New”-FileSystem NTFS – Full -Force -Confirm:$false
Which of the following is the malware using to execute the attack?-
A. PowerShell
-
B. Python
-
C. Bash
-
D. Macros
Correct Wrong
PowerShell is a scripting language and command-line shell that can be used to automate tasks and manage systems. PowerShell can also be used by malware to execute malicious commands and evade detection. The code snippet in the question is a PowerShell command that creates a new partition on disk 2, formats it with NTFS file system, and assigns it a drive letter C. This could be part of an attack that wipes out the original data on the disk or creates a hidden partition for storing malware or stolen data. References: https://www.professormesser.com/security-plus/sy0-601/sy0-601-video/scripting-and-automation/ https://learn.microsoft.com/en-us/powershell/module/storage/new-partition?view=windowsserver2022-ps
-
-
Pytanie z
An attacker is trying to gain access by installing malware on a website that is known to be visited by the target victims. Which of the following is the attacker most likely attempting?
-
A. A spear-phishing attach
-
B. A watering-hole attack
-
C. Typo squatting
-
D. A phishing attack
Correct Wrong
The attacker is most likely attempting a watering-hole attack. A watering-hole attack is a type of attack that targets a specific group of users by compromising a website that they frequently visit. The attacker then installs malware on the website that infects the visitors’ devices or redirects them to malicious sites. The attacker hopes to gain access to the users’ credentials, data, or networks by exploiting their trust in the legitimate website2.
-
-
Pytanie z
A company wants to ensure that all employees in a given department are trained on each job role to help with employee burnout and continuity of business operations in the event an employee leaves the company. Which of the following should the company implement?
-
A. Separation of duties
-
B. Job rotation
-
C. Mandatory vacations
-
D. Least privilege
Correct Wrong
Job rotation is the practice of regularly transitioning employees between different job roles to ensure they gain exposure to various departments and skills. Job rotation can help with employee burnout by providing variety and challenge, and with continuity of business operations by creating backups and cross-trained staff
-
-
Pytanie z
An employee finds a USB flash drive labeled „Salary Info” in an office parking lot. The employee picks up the USB flash drive, goes into the office, and plugs it into a laptop. Later, a technician inspects the laptop and realizes it has been compromised by malware. Which of the following types of social engineering attacks has occurred?
-
A. Smishing
-
B. Baiting
-
C. Tailgating
-
D. Pretexting
Correct Wrong
-
-
Pytanie z
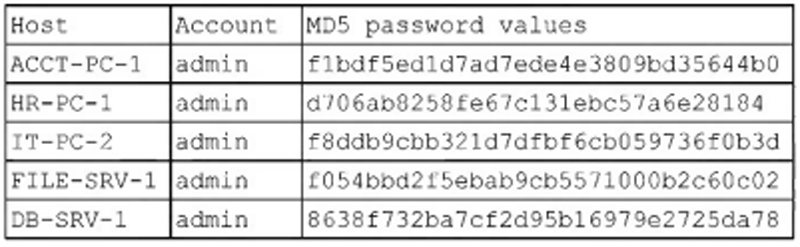
A security administrator recently reset local passwords and the following values were recorded in the system: Which of the following is the security administrator most likely protecting against?

-
A. Account sharing
-
B. Weak password complexity
-
C. Pass-the-hash attacks
-
D. Password compromise
Correct Wrong
-
-
Pytanie z
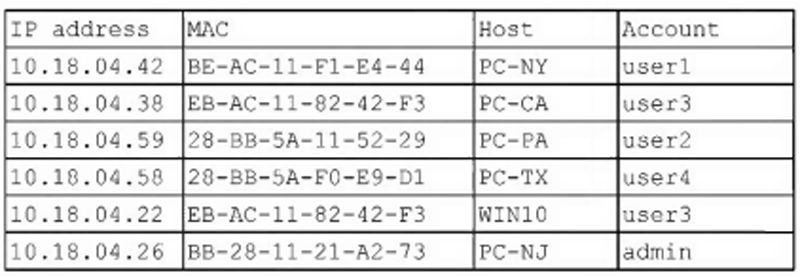
A security analyst finds a rogue device during a monthly audit of current endpoint assets that are connected to the network. The corporate network utilizes 802.1X for access control. To be allowed on the network, a device must have a known hardware address, and a valid username and password must be entered in a captive portal. The following is the audit report: (photo). Which of the following is the most likely way a rogue device was allowed to connect?

-
A. A user performed a MAC cloning attack with a personal device.
-
B. A DHCP failure caused an incorrect IP address to be distributed.
-
C. An administrator bypassed the security controls for testing.
-
D. DNS hijacking let an attacker intercept the captive portal traffic.
Correct Wrong
-


GIPHY App Key not set. Please check settings