-
Pytanie z
A cybersecurity team has witnessed numerous vulnerability events recently that have affected operating systems. The team decides to implement host-based IPS, firewalls, and two-factor authentication. Which of the following does this most likely describe?
-
A. System hardening
-
B. Hybrid network architecture
-
C. Continuous authorization
-
D. Secure access service edge
Correct Wrong
-
-
Pytanie z
A web application team notifies a SOC analyst that there are thousands of HTTP/404 events on the public-facing web server. Which of the following is the next step for the analyst to take?
-
A. Instruct the firewall engineer that a rule needs to be added to block this external server.
-
B. Escalate the event to an incident and notify the SOC manager of the activity.
-
C. Notify the incident response team that a DDoS attack is occurring.
-
D. Identify the IP/hostname for the requests and look at the related activity.
Correct Wrong
A HTTP/404 error code means that the requested page or resource was not found on the web server. This could be caused by various reasons, such as incorrect URLs, moved or deleted pages, missing assets, or server misconfigurations123. The analyst should first identify the source of the requests and examine the related activity to determine if they are legitimate or malicious, and what actions need to be taken to resolve the issue. The other options are either premature or irrelevant without further investigation. References: 1: 404 Page Not Found Error: What It Is and How to Fix It 2: 404 Error Code: What Causes Them and How To Fix It 3: About 404 errors and how to Troubleshoot it?
-
-
Pytanie z
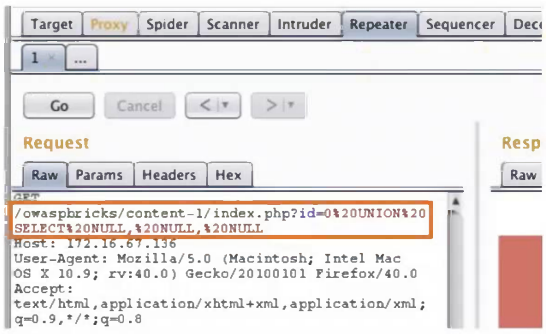
A penetration tester is conducting a test on an organization’s software development website. The penetration tester sends the following request to the web interface: Which of the following exploits is most likely being attempted?

-
A. SQL injection
-
B. Local file inclusion
-
C. Cross-site scripting
-
D. Directory traversal
Correct Wrong
SQL injection is a type of attack that injects malicious SQL statements into a web application’s input fields or parameters, in order to manipulate or access the underlying database. The request shown in the image contains an SQL injection attempt, as indicated by the “UNION SELECT” statement, which is used to combine the results of two or more queries. The attacker is trying to extract information from the database by appending the malicious query to the original one
-
-
Pytanie z
During a cybersecurity incident, one of the web servers at the perimeter network was affected by ransomware. Which of the following actions should be performed immediately?
-
A. Shut down the server.
-
B. Reimage the server
-
C. Quarantine the server
-
D. Update the OS to latest version.
Correct Wrong
Quarantining the server is the best action to perform immediately, as it isolates the affected server from the rest of the network and prevents the ransomware from spreading to other systems or data. Quarantining the server also preserves the evidence of the ransomware attack, which can be useful for forensic analysis and law enforcement investigation. The other actions are not as urgent as quarantining the server, as they may not stop the ransomware infection, or they may destroy valuable evidence. Shutting down the server may not remove the ransomware, and it may trigger a data deletion mechanism by the ransomware. Reimaging the server may restore its functionality, but it will also erase any traces of the ransomware and make recovery of encrypted data impossible. Updating the OS to the latest version may fix some vulnerabilities, but it will not remove the ransomware or decrypt the data. Official References: https://www.cisa.gov/stopransomware/ransomware-guide https://www.cisa.gov/sites/default/files/publications/Ransomware_Executive_One-Pager_and_Technical_ https://www.cisa.gov/stopransomware/ive-been-hit-ransomware
-
-
Pytanie z
An organization enabled a SIEM rule to send an alert to a security analyst distribution list when ten failed logins occur within one minute. However, the control was unable to detect an attack with nine failed logins. Which of the following best represents what occurred?
-
A. False positive
-
B. True negative
-
C. False negative
-
D. True positive
Correct Wrong
The correct answer is C. False negative. A false negative is a situation where an attack or a threat is not detected by a security control, even though it should have been. In this case, the SIEM rule was unable to detect an attack with nine failed logins, which is below the threshold of ten failed logins that triggers an alert. This means that the SIEM rule missed a potential attack and failed to alert the security analysts, resulting in a false negative. A false positive is a situation where a benign or normal activity is detected as an attack or a threat by a security control, even though it is not. A true negative is a situation where a benign or normal activity is not detected as an attack or a threat by a security control, as expected. A true positive is a situation where an attack or a threat is detected by a security control, as expected. These are not the correct answers for this question.
-
-
Pytanie z
A security analyst discovers an ongoing ransomware attack while investigating a phishing email. The analyst downloads a copy of the file from the email and isolates the affected workstation from the network. Which of the following activities should the analyst perform next?
-
A. Wipe the computer and reinstall software
-
B. Shut down the email server and quarantine it from the network.
-
C. Acquire a bit-level image of the affected workstation.
-
D. Search for other mail users who have received the same file.
Correct Wrong
Searching for other mail users who have received the same file is the best activity to perform next, as it helps to identify and contain the scope of the ransomware attack and prevent further damage. Ransomware is a type of malware that encrypts files on a system and demands payment for their decryption. Ransomware can spread through phishing emails that contain malicious attachments or links that download the ransomware. By searching for other mail users who have received the same file, the analyst can alert them not to open it, delete it from their inboxes, and scan their systems for any signs of infection. The other activities are not as urgent or effective as searching for other mail users who have received the same file, as they do not address the immediate threat of ransomware spreading or affecting more systems. Wiping the computer and reinstalling software may restore the functionality of the affected workstation, but it will also erase any evidence of the ransomware attack and make recovery of encrypted files impossible. Shutting down the email server and quarantining it from the network may stop the delivery of more phishing emails, but it will also disrupt normal communication and operations for the organization. Acquiring a bit-level image of the affected workstation may preserve the evidence of the ransomware attack, but it will not help to stop or remove the ransomware or decrypt the files.
-
-
Pytanie z
An analyst recommends that an EDR agent collect the source IP address, make a connection to the firewall, and create a policy to block the malicious source IP address across the entire network automatically. Which of the following is the best option to help the analyst implement this recommendation?
-
A. SOAR
-
B. SIEM
-
C. SLA
-
D. IoC
Correct Wrong
SOAR (Security Orchestration, Automation, and Response) is the best option to help the analyst implement the recommendation, as it reflects the software solution that enables security teams to integrate and coordinate separate tools into streamlined threat response workflows and automate repetitive tasks. SOAR is a term coined by Gartner in 2015 to describe a technology that combines the functions of security incident response platforms, security orchestration and automation platforms, and threat intelligence platforms in one offering. SOAR solutions help security teams to collect inputs from various sources, such as EDR agents, firewalls, or SIEM systems, and perform analysis and triage using a combination of human and machine power. SOAR solutions also allow security teams to define and execute incident response procedures in a digital workflow format, using automation to perform low-level tasks or actions, such as blocking an IP address or quarantining a device. SOAR solutions can help security teams to improve efficiency, consistency, and scalability of their operations, as well as reduce mean time to detect (MTTD) and mean time to respond (MTTR) to threats. The other options are not as suitable as SOAR, as they do not match the description or purpose of the recommendation. SIEM (Security Information and Event Management) is a software solution that collects and analyzes data from various sources, such as logs, events, or alerts, and provides security monitoring, threat detection, and incident response capabilities. SIEM solutions can help security teams to gain visibility, correlation, and context of their security data, but they do not provide automation or orchestration features like SOAR solutions. SLA (Service Level Agreement) is a document that defines the expectations and responsibilities between a service provider and a customer, such as the quality, availability, or performance of the service. SLAs can help to manage customer expectations, formalize communication, and improve productivity and relationships, but they do not help to implement technical recommendations like SOAR solutions. IoC (Indicator of Compromise) is a piece of data or evidence that suggests a system or network has been compromised by a threat actor, such as an IP address, a file hash, or a registry key. IoCs can help to identify and analyze malicious activities or incidents, but they do not help to implement response actions like SOAR solutions.
-
-
Pytanie z
An email hosting provider added a new data center with new public IP addresses. Which of the following most likely needs to be updated to ensure emails from the new data center do not get blocked by spam filters?
-
A. DKIM
-
B. SPF
-
C. SMTP
-
D. DMARC
Correct Wrong
SPF (Sender Policy Framework) is a DNS TXT record that lists authorized sending IP addresses for a given domain. If an email hosting provider added a new data center with new public IP addresses, the SPF record needs to be updated to include those new IP addresses, otherwise the emails from the new data center may fail SPF checks and get blocked by spam filters123 References: 1: Use DMARC to validate email, setup steps 2: How to set up SPF, DKIM and DMARC: other mail & hosting providers providers 3: Set up SPF, DKIM, or DMARC records for my hosting email
-
-
Pytanie z
Which of the following would a security analyst most likely use to compare TTPs between different known adversaries of an organization?
-
A. MITRE ATTACK
-
B. Cyber Kill Cham
-
C. OWASP
-
D. STIX TAXII
Correct Wrong
-
-
Pytanie z
An analyst is conducting monitoring against an authorized team that win perform adversarial techniques. The analyst interacts with the team twice per day to set the stage for the techniques to be used. Which of the following teams is the analyst a member of?
-
A. Orange team
-
B. Blue team
-
C. Red team
-
D. Purple team
Correct Wrong
An orange team is a team that is involved in facilitation and training of other teams in cybersecurity. An orange team assists the yellow team, which is the management or leadership team that oversees the cybersecurity strategy and governance of an organization. An orange team helps the yellow team to understand the cybersecurity risks and challenges, as well as the roles and responsibilities of other teams, such as the red, blue, and purple teams12. In this scenario, the analyst is conducting monitoring against an authorized team that will perform adversarial techniques. This means that the analyst is observing and evaluating the performance of another team that is simulating real-world attacks against the organization’s systems or networks. This could be either a red team or a purple team, depending on whether they are working independently or collaboratively with the defensive team345. The analyst interacts with the team twice per day to set the stage for the techniques to be used. This means that the analyst is providing guidance and feedback to the team on how to conduct their testing and what techniques to use. This could also involve setting up scenarios, objectives, rules of engagement, and success criteria for the testing. This implies that the analyst is facilitating and training the team to improve their skills and capabilities in cybersecurity12. Therefore, based on these descriptions, the analyst is a member of an orange team, which is involved in facilitation and training of other teams in cybersecurity. The other options are incorrect because they do not match the role and function of the analyst in this scenario. Option B is incorrect because a blue team is a defensive security team that monitors and protects the organization’s systems and networks from real or simulated attacks. A blue team does not conduct monitoring against an authorized team that will perform adversarial techniques, but rather defends against them345. Option C is incorrect because a red team is an offensive security team that discovers and exploits vulnerabilities in the organization’s systems or networks by simulating real-world attacks. A red team does not conduct monitoring against an authorized team that will perform adversarial techniques, but rather performs them345. Option D is incorrect because a purple team is not a separate security team, but rather a collaborative approach between the red and blue teams to improve the organization’s overall security. A purple team does not conduct monitoring against an authorized team that will perform adversarial techniques, but rather works with them345.
-
-
Pytanie z
A new cybersecurity analyst is tasked with creating an executive briefing on possible threats to the organization. Which of the following will produce the data needed for the briefing?
-
A. Firewall logs
-
B. Indicators of compromise
-
C. Risk assessment
-
D. Access control lists
Correct Wrong
Indicators of compromise (IoCs) are pieces of data or evidence that suggest a system or network has been compromised by an attacker or malware. IoCs can include IP addresses, domain names, URLs, file hashes, registry keys, network traffic patterns, user behaviors, or system anomalies. IoCs can be used to detect, analyze, and respond to security incidents, as well as to share threat intelligence with other organizations or authorities. IoCs can produce the data needed for an executive briefing on possible threats to the organization, as they can provide information on the source, nature, scope, impact, and mitigation of the threats.
-
-
Pytanie z
While reviewing the web server logs, a security analyst notices the following snippet: .. .. / .. .. /boot.ini Which of the following Is belng attempted?
-
A. Directory traversal
-
B. Remote file inclusion
-
C. Cross-site scripting
-
D. Remote code execution
-
E. Enumeration of /etc/passwd
Correct Wrong
The snippet shows an attempt to access the boot.ini file, which is a configuration file for Windows operating systems. The “… … /” pattern is used to navigate up the directory structure and reach the root directory, where the boot.ini file is located. This is a common technique for exploiting directory traversal vulnerabilities, which allow an attacker to access files and directories outside the intended web server path. The other options are not relevant for this purpose: remote file inclusion involves injecting a malicious file into a web application; cross-site scripting involves injecting malicious scripts into a web page; remote code execution involves executing arbitrary commands on a remote system; enumeration of /etc/passwd involves accessing the file that stores user information on Linux systems. References: According to the CompTIA CySA+ Study Guide: Exam CS0-003, 3rd Edition1, one of the objectives for the exam is to “use appropriate tools and methods to manage, prioritize and respond to attacks and vulnerabilities”. The book also covers the usage and syntax of web server logs, which record the requests and responses of web applications, in chapter 6. Specifically, it explains the meaning and function of each component in web server logs, such as the HTTP method, the URL, the status code, and the user agent1, page 244. It also discusses the common types and indicators of web-based attacks, such as directory traversal, which use special characters to manipulate the web server path1, page 251. Therefore, this is a reliable source to verify the answer to the question.
-
-
Pytanie z
A security analyst has received an incident case regarding malware spreading out of control on a customer’s network. The analyst is unsure how to respond. The configured EDR has automatically obtained a sample of the malware and its signature. Which of the following should the analyst perform next to determine the type of malware, based on its telemetry?
-
A. Cross-reference the signature with open-source threat intelligence.
-
B. Configure the EDR to perform a full scan.
-
C. Transfer the malware to a sandbox environment.
-
D. Log in to the affected systems and run necstat.
Correct Wrong
The signature of the malware is a unique identifier that can be used to compare it with known malware samples and their behaviors. Open-source threat intelligence sources provide information on various types of malware, their indicators of compromise, and their mitigation strategies. By cross-referencing the signature with these sources, the analyst can determine the type of malware and its telemetry. The other options are not relevant for this purpose: configuring the EDR to perform a full scan may not provide additional information on the malware type; transferring the malware to a sandbox environment may expose the analyst to further risks; logging in to the affected systems and running netstat may not reveal the malware activity. References: According to the CompTIA CySA+ Study Guide: Exam CS0-003, 3rd Edition1, one of the objectives for the exam is to “use appropriate tools and methods to manage, prioritize and respond to attacks and vulnerabilities”. The book also covers the usage and syntax of EDR, a tool used for endpoint security, in chapter 5. Specifically, it explains the meaning and function of malware signatures and how they can be used to identify malware types1, page 203. It also discusses the benefits and challenges of using open-source threat intelligence sources to enhance security analysis1, page 211. Therefore, this is a reliable source to verify the answer to the question
-
-
Pytanie z
During an incident involving phishing, a security analyst needs to find the source of the malicious email. Which of the following techniques would provide the analyst with this information?
-
A. Header analysis
-
B. Packet capture
-
C. SSL inspection
-
D. Reverse engineering
Correct Wrong
Header analysis is the technique of examining the metadata of an email, such as the sender, recipient, date, subject, and routing information. It can help to identify the source of a malicious email by revealing the IP address and domain name of the originator, as well as any spoofing or redirection attempts. References: CompTIA CySA+ Study Guide: Exam CS0-003, 3rd Edition, Chapter 6, page 240; CompTIA CySA+ CS0-003 Certification Study Guide, Chapter 6, page 249.
-
-
Pytanie z
A security analyst is reviewing the findings of the latest vulnerability report for a company’s web application. The web application accepts files for a Bash script to be processed if the files match a given hash. The analyst is able to submit files to the system due to a hash collision. Which of the following should the analyst suggest to mitigate the vulnerability with the fewest changes to the current script and infrastructure?
-
A. Deploy a WAF to the front of the application.
-
B. Replace the current MD5 with SHA-256.
-
C. Deploy an antivirus application on the hosting system.
-
D. Replace the MD5 with digital signatures.
Correct Wrong
The vulnerability that the security analyst is able to exploit is a hash collision, which is a situation where two different files produce the same hash value. Hash collisions can allow an attacker to bypass the integrity or authentication checks that rely on hash values, and submit malicious files to the system. The web application uses MD5, which is a hashing algorithm that is known to be vulnerable to hash collisions. Therefore, the analyst should suggest replacing the current MD5 with SHA-256, which is a more secure and collision-resistant hashing algorithm. The other options are not the best suggestions to mitigate the vulnerability with the fewest changes to the current script and infrastructure. Deploying a WAF (web application firewall) to the front of the application (A) may help protect the web application from some common attacks, but it may not prevent hash collisions or detect malicious files. Deploying an antivirus application on the hosting system © may help scan and remove malicious files from the system, but it may not prevent hash collisions or block malicious files from being submitted. Replacing the MD5 with digital signatures (D) may help verify the authenticity and integrity of the files, but it may require significant changes to the current script and infrastructure, as digital signatures involve public-key cryptography and certificate authorities.
-


GIPHY App Key not set. Please check settings