-
Pytanie z
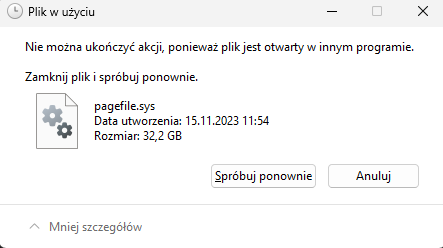
Charles wants to perform memory forensics on a Windows system and wants to access pagefile.sys. When he attempts to copy it, he receives the following error. What access method is required to access the page file?

-
Run Windows File Explorer as an administrator and repeat the copy.
-
Open the file using „fmem”.
-
Run cmd.exe as an administrator and repeat the copy.
-
Shut the system down, remove the drive, and copy it from another system.
Correct Wrong
Wyłączyć system brutalną mocą! | fmem - moduł jądra Linux, który umożliwia bezpośredni dostęp do pamięci fizycznej systemu. Tworzy on wirtualne urządzenie /dev/fmem, które pozwala na uzyskanie pełnego obrazu pamięci RAM
-
-
Pytanie z
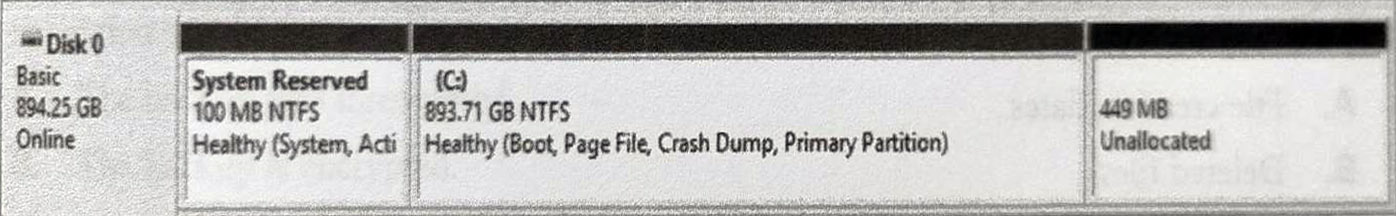
Where is slack space found in the following Windows partition map?

-
The System Reserved partition
-
The System Reserved and Unnallocated partitions
-
The System Reserved and C: partitions
-
The C: and unallocated partitions
Correct Wrong
Slack space is leftover storage that exists because files do not take up the entire space allocated form them. Since the Unallocated partition does not have a filesystem on it, space there should not be considered slack space. Both System Reserved and C: are formatted with NTFS an will have slack space between files. -------------------- Termin „Slack space” w języku polskim najczęściej tłumaczy się jako „przestrzeń szczątkowa” lub „luźna przestrzeń”. Odnosi się on do nieużywanego obszaru na dysku twardym, który znajduje się pomiędzy końcem pliku a końcem przydzielonego mu klastra.-------------Przestrzeń szczątkowa: W systemach plików, pliki są przechowywane w jednostkach zwanych klastrami. Jeśli plik nie wypełnia całego klastra, reszta tej przestrzeni pozostaje niewykorzystana. Ta niewykorzystana przestrzeń nazywana jest przestrzenią szczątkową. Na przykład, jeśli plik zajmuje 1000 bajtów, a rozmiar klastra to 4096 bajtów, to 3096 bajtów pozostaje nieużywane.
-
-
Pytanie z
The ATT&CK framework defines which of the following as „the specifics behind how the adversary would attack the target”?
-
The threat actor
-
The targeting method
-
The attack vector
-
The organizational weakness
Correct Wrong
-
-
Pytanie z
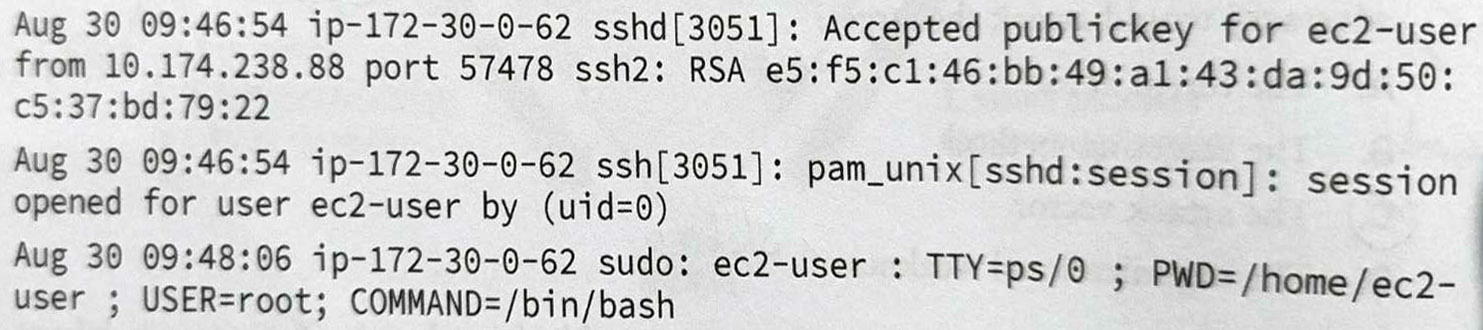
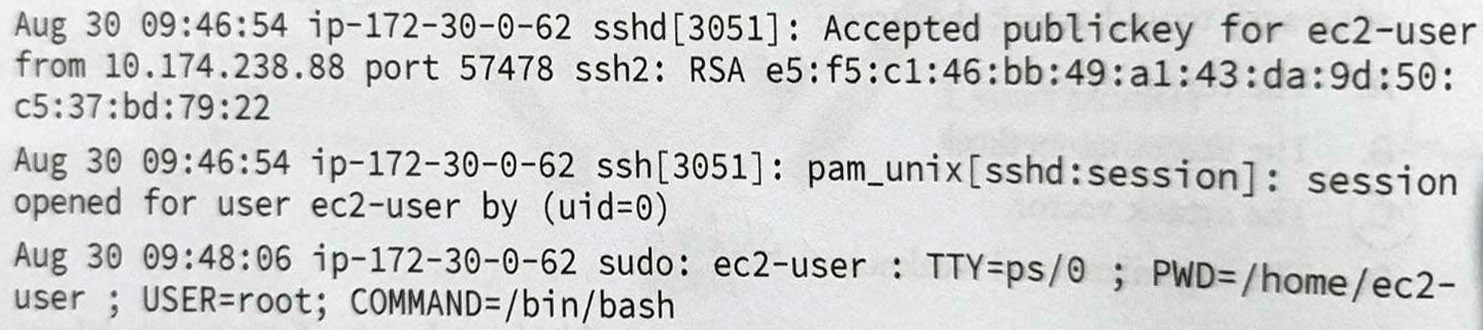
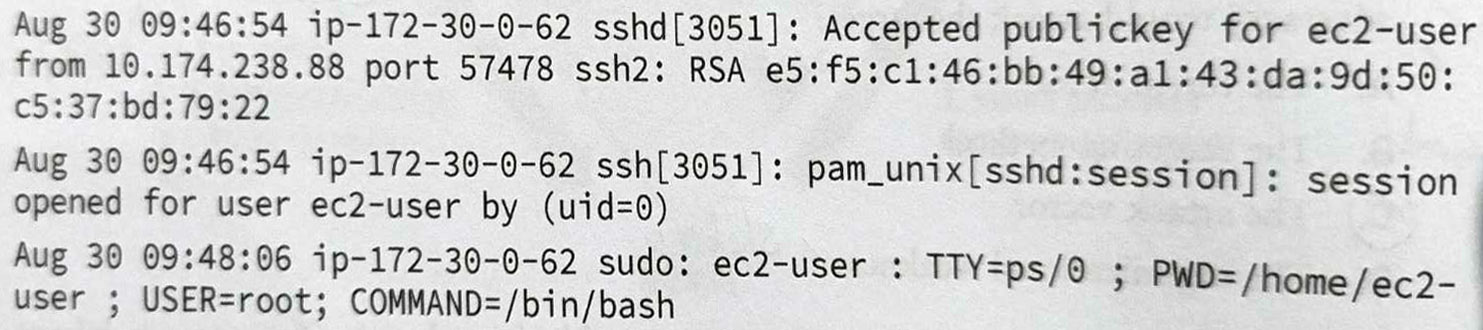
Question 4-7 refer to the following scenario and image.
Bill is reviewing the authentication logs for Linux system that he operates and encounters the following log entries:
What is the IP address of the system where the user was logged in when they initiated the connection?
-
172.30.0.62
-
62.0.30.172
-
10.174.238.88
-
9.48.6.0
Correct Wrong
-
-
Pytanie z
What service did the user use to connect to the server?

-
HTTPS
-
PTS
-
SSH
-
Telnet
Correct Wrong
-
-
Pytanie z
What authentication technique did the user use to connect to the server?

-
Password
-
PKI
-
Token
-
Biometric
Correct Wrong
PKI (Public Key Infrastructure) to system zarządzania kluczami kryptograficznymi, który umożliwia bezpieczną wymianę informacji w środowiskach cyfrowych. -------------------------- The first log entry indicates that the user made use of public key encryption (PKI) to authenticate the connection. The user, therefore, possessed the private key that corresponded to a public key stored on the server and associated with the user.-------------------Pierwszy wpis w dzienniku wskazuje, że użytkownik użył szyfrowania klucza publicznego (PKI) do uwierzytelnienia połączenia. Użytkownik posiadał zatem klucz prywatny, który odpowiadał kluczowi publicznemu przechowywanemu na serwerze i powiązanemu z użytkownikiem.
-
-
Pytanie z
What account did the individual use to connect to the server?

-
root
-
ec2-user
-
bash
-
pam_unix
Correct Wrong
-
-
Pytanie z
When analyzing network traffic for indicators of compromise, which one of the following service/port pairings would indicate a common protocol running on a nonstandard port?
-
HTTPS on TCP port 443
-
RDP on TCP port 3389
-
SSH on TCP port 1433
-
HTTP on TCP port 80
Correct Wrong
-
-
Pytanie z
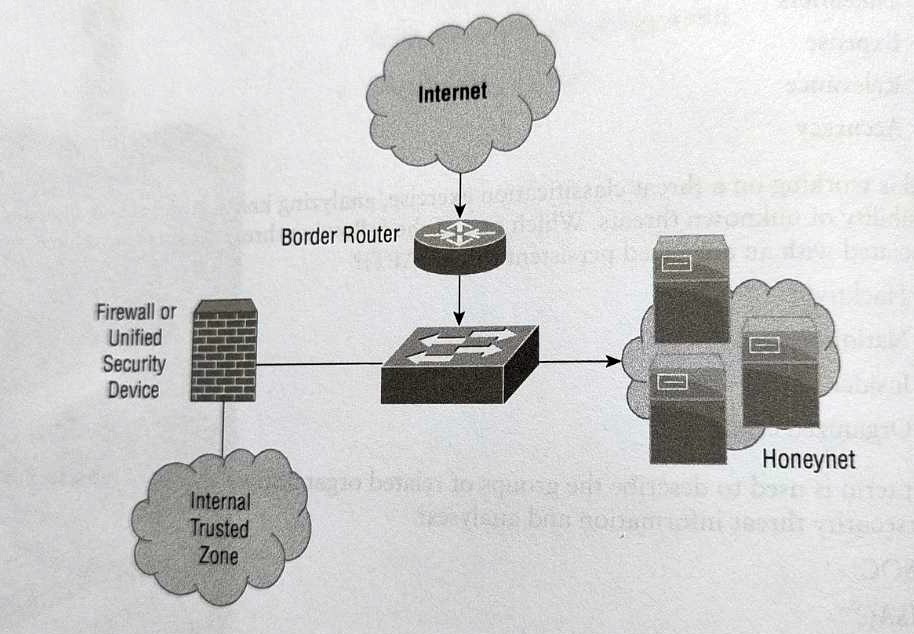
Lauren’s honeynet, show here, is configured to use a segment of unused network space that has no legitimate servers in it. This design is particulary useful for detecting what types of threats?

-
Zero-day attacks
-
SQL injection
-
Network scans
-
DDoS attacks
Correct Wrong
Detection systems placed in otherwise unused network space will detect scans that blindly traverse IP address ranges. Since no public services are listed, attackers who scan this range can be presumed to be hostile and are often immediately blocked by security davices that protect production systems. ------------- Systemy wykrywania umieszczone w nieużywanej przestrzeni sieciowej wykryją skanowanie, które bezmyślnie przechodzi przez zakresy adresów IP. Ponieważ na liście nie ma żadnych usług publicznych, można założyć, że osoby atakujące skanujące ten obszar są wrogie i często są natychmiast blokowane przez urządzenia zabezpieczające chroniące systemy produkcyjne.
-
-
Pytanie z
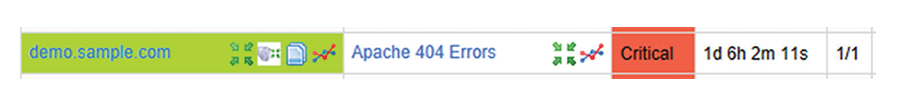
While reviewing her Nagios logs, Selah discovers the error message shown here. What should she do about this error?

-
Check for evidence of a port scan.
-
Review the Apache error log.
-
Reboot the server to restore the service.
-
Restart the Apache service.
Correct Wrong
Selah should check the error log to determine what web page or file access resulted in 404 “not found” errors. The errors may indicate that a page is mislinked, but it may also indicate a scan occurring against her web server.
-
-
Pytanie z
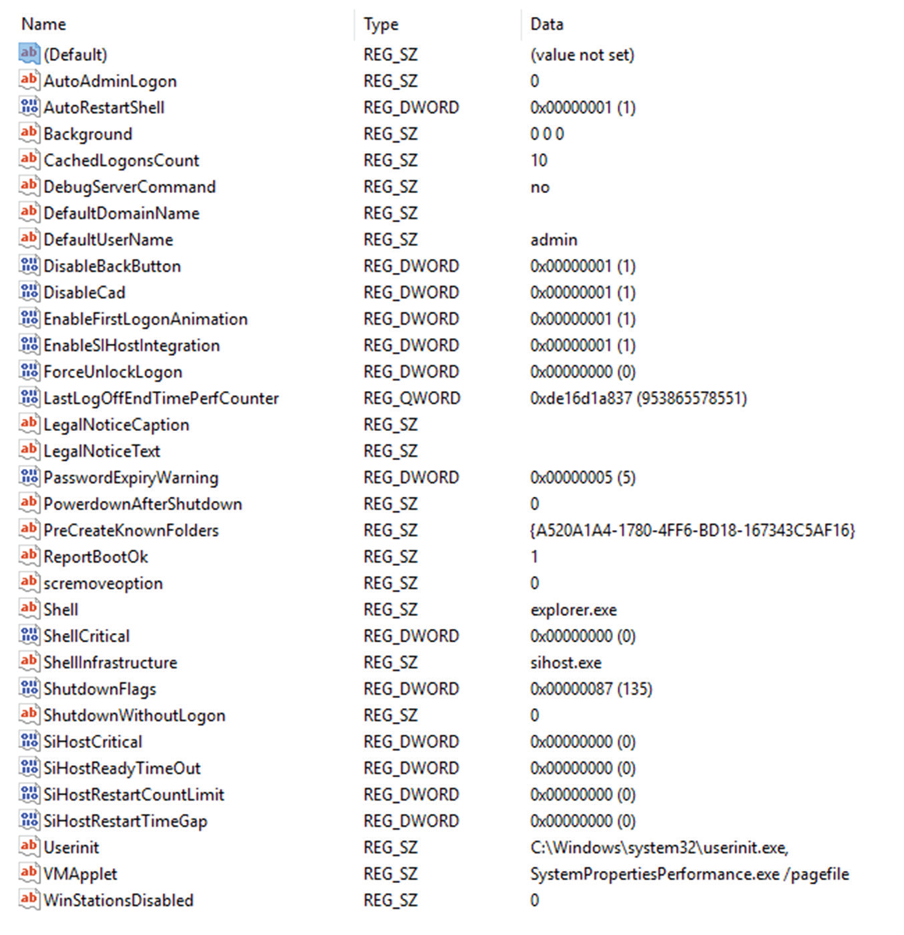
During her forensic analysis of a Windows system, Cynthia accesses the registry and checks HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsNTCurrentVersion Winlogin. What domain was the system connected to, and what was the username that would appear at login?

-
Admin, administrator
-
No domain, admin
-
Legal, admin
-
Corporate, no default username
Correct Wrong
This system is not connected to a domain (default domain name has no value), and the default user is admin.
-
-
Pytanie z
Lauren recovers a number of 16GB and 32GB microSD cards during a forensic investigation. Without checking them manually, what filesystem type is she most likely to find them formatted in as if they were used with a digital camera?
-
RAW
-
FAT16
-
FAT32
-
HFS+
Correct Wrong
Most portable consumer devices, especially those that generate large files, format their storage as FAT32. FAT16 is limited to 2GB partitions, RAW is a photo file format, and HFS+ is the native macOS file format. Lauren can expect most devices to format media as FAT32 by default because of its broad compatibility across devices and operating systems.
-
-
Pytanie z
Scott needs to verify that the forensic image he has created is an exact duplicate of the original drive. Which of the following methods is considered forensically sound?
-
Create a MD5 hash
-
Create a SHA-1 hash
-
Create a SHA-2 hash
-
All of the above
Correct Wrong
MD5, SHA-1, and SHA-2 hashes are all considered forensically sound. While MD5 hashes are no longer a secure means of hashing, they are still considered appropriate for validation of forensic images because it is unlikely that an attacker would intentionally create a hash collision to falsify the forensic integrity of a drive.
-
-
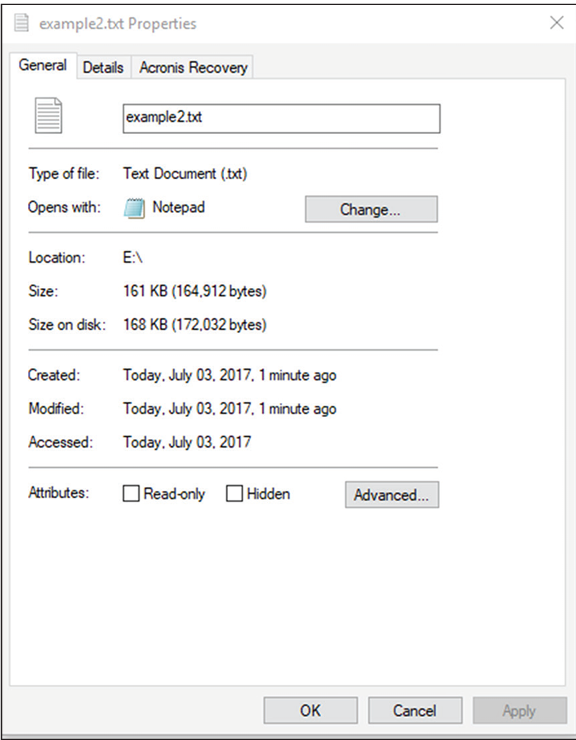
Pytanie z
Saria is reviewing the contents of a drive as part of a forensic effort and notes that the file she is reviewing takes up more space on the disk than its actual size, as shown here. What has she discovered?

-
Slack space
-
Hidden content
-
Sparse files
-
Encryption overhead
Correct Wrong
The space that Saria sees is the space between the end of the file and the space allocated per cluster or block. This space may contain remnants of previous files written to the cluster or block or may simply contain random data from when the disk was formatted or initialized.
-
-
Pytanie z
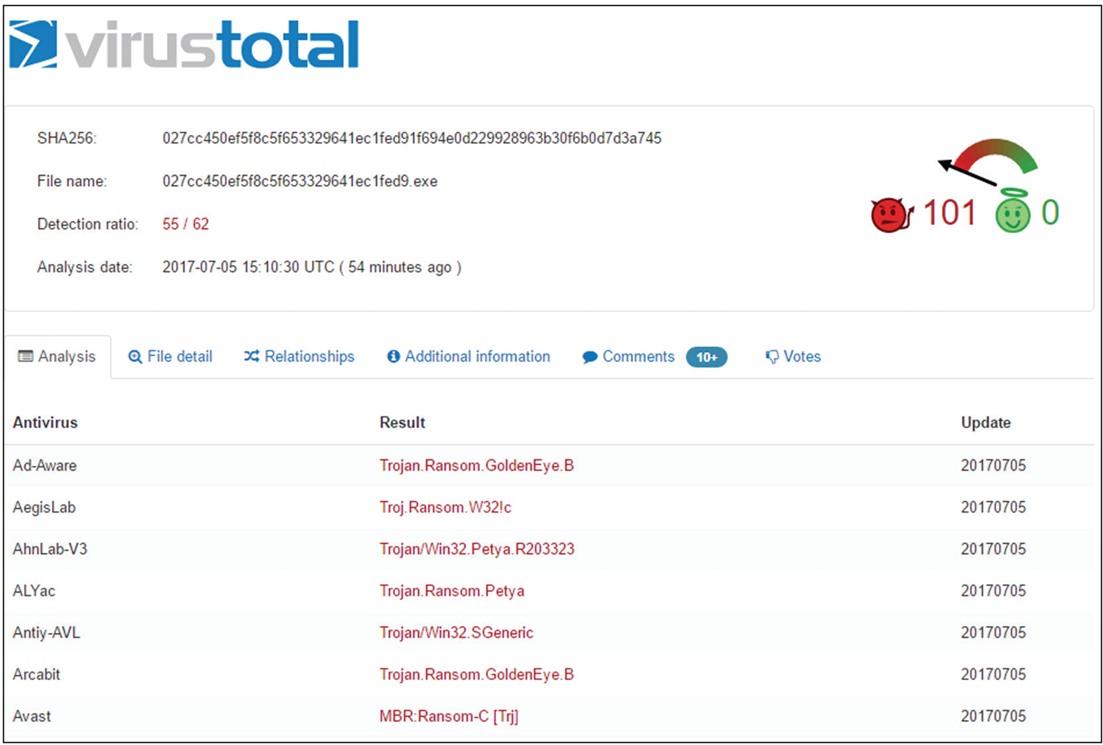
After submitting a suspected malware package to VirusTotal, Alex receives the following results. What does this tell Alex?

-
The submitted file contains more than one malware package.
-
Antivirus vendors use different names for the same malware.
-
VirusTotal was unable to specifically identify the malware.
-
VirusTotal was unable to specifically identify the malware.
Correct Wrong
Each antivirus or anti-malware vendor uses their own name for malware, resulting in a variety of names showing for a given malware package or family. In this case, the malware package is a ransomware package; that is known by some vendors as GoldenEye or Petya.
-
-
Pytanie z
Which forensic imaging tool is already installed on most Linux operating systems?
-
FTK
-
OSFClone
-
EnCase
-
dd
Correct Wrong
All of the tools listed have forensic imaging capabilities, but dd is a disk duplicating tool that is built into most Linux systems.
-
-
Pytanie z
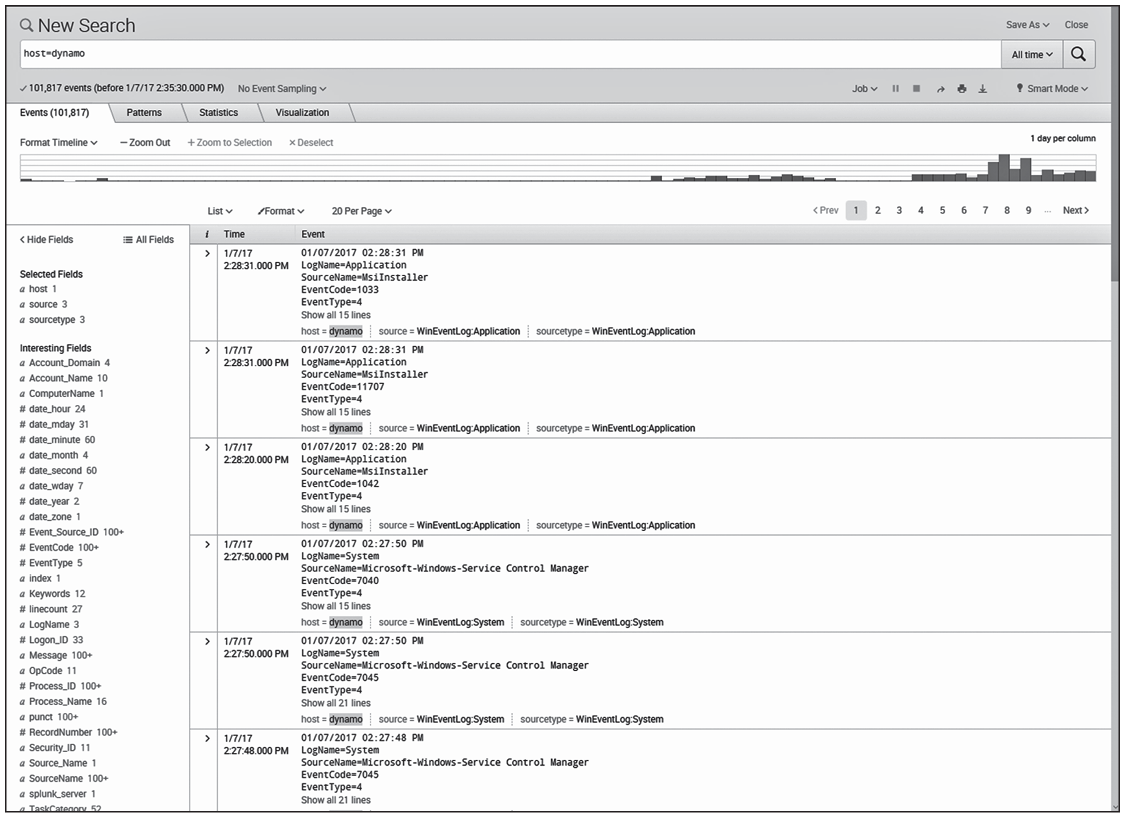
Simon would like to use a cybersecurity analysis tool that facilitates searching through massive quantities of log information in a visual manner. He has a colleague who uses the tool shown here. What tool would best meet Simon’s needs?

-
Syslog
-
Kiwi
-
Splunk
-
Sysinternals
Correct Wrong
The interface shown in the picture is Splunk, a SIEM that specializes in visual search and allows analysts to comb through massive quantities of information in an intuitive way. Kiwi and other Syslog tools allow the collection and analysis of this information but do not provide the visual interface used in Splunk. Sysinternals does not include a log analysis tool.
-
-
Pytanie z
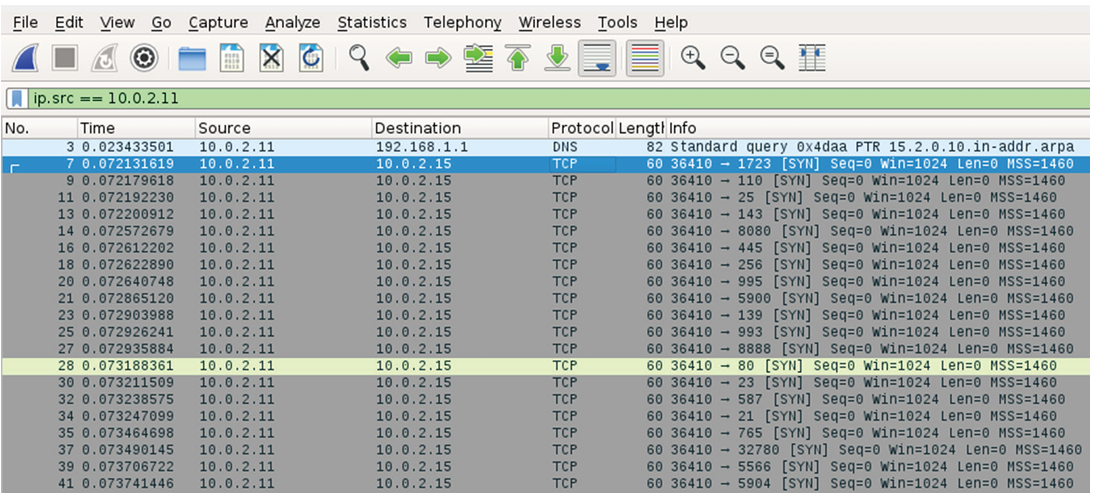
Alex notices the traffic shown here during a Wireshark packet capture. What is the host with IP address 10.0.2.11 most likely doing?

-
UDP-based port scanning
-
Network discovery via TCP
-
SYN based port scanning
-
DNS based discovery
Correct Wrong
This image shows a SYN-based port scan. The traffic is primarily made up of TCP SYN packets to a variety of common ports, which is typical of a SYN-based port scan.
-
-
Pytanie z
Frank discovered during a vulnerability scan that an administrative interface to one of his storage systems was inadvertently exposed to the Internet. He is reviewing firewall logs and would like to determine whether any access attempts came from external sources. Which one of the following IP addresses reflects an external source?
-
10.15.1.100
-
12.8.1.100
-
172.16.1.100
-
192.168.1.100
Correct Wrong
Any addresses in the 10.x.x.x, 172.16.x.x, and 192.168.x.x ranges are private IP addresses that are not routable over the Internet. Therefore, of the addresses listed, only 12.8.1.100 could originate outside the local network.
-
-
Pytanie z
Chris wants to run John the Ripper against a Linux system’s passwords. What does he need to attempt password recovery on the system?
-
Both /etc/passwd and /etc/shadow
-
/etc/shadow
-
/etc/passwd
-
Chris cannot recover passwords; only hashes are stored.
Correct Wrong
Chris needs both /etc/passwd and /etc/shadow for John to crack the passwords. While only hashes are stored, John the Ripper includes built-in brute-force tools that will crack the passwords.
-
-
Pytanie z
Which of the following properly lists the order of volatility from least volatile to most volatile?
-
Printouts, swap files, CPU cache, RAM
-
Hard drives, USB media, DVDs, CD-RWs
-
DVDs, hard drives, virtual memory, caches
-
RAM, swap files, SSDs, printouts
Correct Wrong
The order of volatility for media from least to most volatile is often listed as backups and printouts; then disk drives like hard drives and SSDs; then virtual memory; and finally CPU cache, registers, and RAM. Artifacts stored in each of these locations can be associated with the level of volatility of that storage mechanism. For example, routing tables will typically be stored in RAM, making them highly volatile. Data stored on a rewriteable media is always considered more volatile than media stored on a write-only media.--------------------------- Kolejność lotności nośników od najmniej do najbardziej lotnych jest często wymieniana jako: kopie zapasowe i wydruki; następnie dyski, takie jak dyski twarde i SSD; potem pamięć wirtualna; a na końcu pamięć podręczna CPU, rejestry i RAM. Artefakty przechowywane w każdej z tych lokalizacji mogą być związane z poziomem lotności danego mechanizmu przechowywania. Na przykład, tablice routingu są zazwyczaj przechowywane w RAM, co czyni je wysoce lotnymi. Dane przechowywane na nośnikach, które można ponownie zapisywać, są zawsze uważane za bardziej lotne niż dane przechowywane na nośnikach, które można tylko zapisać raz.
-
-
Pytanie z
Joe wants to recovery the passwords for local Windows users on a Windows 7 workstation. Where are the password hashes stored?
-
C:WindowsSystem32passwords
-
C:WindowsSystem32config
-
C:WindowsSecureconfig
-
C:WindowsSecureaccounts
Correct Wrong
The SAM is stored in C:WindowsSystem32config but is not accessible while the system is booted. The hashed passwords are also stored in the registry at HKEY_LOCAL_ MACHINESAM but are also protected while the system is booted. The best way to recover the SAM is by booting off of removable media or using a tool like fgdump.
-
-
Pytanie z
While conducting a forensic review of a system involved in a data breach, Alex discovers a number of Microsoft Word files including files with filenames like critical_data.docx and sales_estimates_2017.docx. When he attempts to review the files using a text editor for any useful information, he finds only unreadable data. What has occurred?
-
Microsoft Word files are stored in .zip format.
-
Microsoft Word files are encrypted.
-
Microsoft Word files can be opened only by Microsoft Word.
-
The user has used antiforensic techniques to scramble the data.
Correct Wrong
-
-
Pytanie z
Terrence remotely connected to a Linux system and is attempting to determine the active network connections on that system. What command can he use to most easily discover this information?
-
ifconfig
-
tcpdump
-
iptables
-
ipconfig
Correct Wrong
The ifconfig command displays information about network interfaces on a Linux system. The ipconfig command displays similar information on Windows systems. tcpdump is a packet capture tool and iptables is a Linux firewall.
-
-
Pytanie z
A large enterprise has moved all its data to the cloud behind strong authentication and encryption. A sales director recently had a laptop stolen, and later, enterprise data was found to have been compromised from a local database. Which of the following was the MOST likely cause?

-
A. Shadow IT
-
B. Credential stuffing
-
C. SQL injection
-
D. Man in the browser
Correct Wrong
-
-
Pytanie z
A global pandemic is forcing a private organization to close some business units and reduce staffing at others. Which of the following would be best to help the organization’s executives determine their next course of action?
-
. An incident response plan
-
B. A communication plan
-
C. A disaster recovery plan
-
D. A business continuity plan
Correct Wrong
-
-
Pytanie z
An analyst is concerned about data leaks and wants to restrict access to internet services to authorized users only. The analyst also wants to control the actions each user can perform on each service. Which of the following would be the best technology for the analyst to consider implementing?
-
A. DLP
-
B. VPC
-
C. CASB
-
D. Content filtering
Correct Wrong
-
-
Pytanie z
A company wants to move one of its environments to the cloud. The biggest requirement is to have as much control as possible regarding the environment. Which of the following would most likely satisfy this requirement?
-
A. SaaS
-
B. laaS
-
C. PaaS
-
D. MaaS
Correct Wrong
-
-
Pytanie z
A worldwide manufacturing company has been experiencing email account compromises. In one incident, a user logged in from the corporate office in France, but then seconds later, the same user account attempted a login from Brazil. Which of the following account policies would best prevent this type of attack?
-
A. Network location
-
B. Impossible travel time
-
C. Geolocation
-
D. Geofencing
Correct Wrong
-
-
Pytanie z
Which Of the following will provide the best physical security countermeasures to Stop intruders? (Select two).
-
A. Alarm
-
B. Signage
-
C. Lighting
-
D. Access control vestibules
-
E. Fencing
-
F. Sensors
Correct Wrong
D i E
-
-
Pytanie z
Which of the following function as preventive, detective, and deterrent controls to reduce the risk of physical theft? (Select TWO).
-
A. Mantraps
-
B. Security guards
-
C. Video surveillance
-
D. Fences
-
E. Bollards
-
F. Antivirus
Correct Wrong
A i D
-
-
Pytanie z
A company is concerned about individuals driving a car into the building to gam access Which of the following security controls would work BEST to prevent this from happening?
-
A. Bollard
-
B. Camera
-
C. Alarms
-
D. Signage
-
E. Access control vestibule
Correct Wrong
-
-
Pytanie z
A security analyst has received several reports of an issue on an internal web application. Users state they are having to provide their credentials twice to log in. The analyst checks with the application team and notes this is not an expected behavior. After looking at several logs, the analyst decides to run some commands on the gateway and obtains the following output: Which of the following BEST describes the attack the company is experiencing?

-
A. MAC flooding
-
B. URL redirection
-
C. ARP poisoning
-
D. DNS hijacking
Correct Wrong
-




GIPHY App Key not set. Please check settings