-
Pytanie z
A company has established an email client on the network using POP3. The company wants a way to digitally sign all emails leaving the organization to uphold its worldwide reputation. Which of the following BEST describes this process?
-
A. SPF
-
B. DMARC
-
C. DKIM
-
D. RADIUS
Correct Wrong
DKIM (DomainKeys Identified Mail) is a method used to digitally sign outgoing emails to verify the authenticity of the sender and ensure the integrity of the message. By adding a digital signature to each outgoing email, DKIM helps prevent email tampering and forgeries, making it the best choice for digitally signing emails leaving the organization.
-
-
Pytanie z
A cybersecurity is having its organization tested by a penetration testing firm. The penetration tester identifies SMBv1 running as a vulnerable service on all Windows devices in the organization. To which of the following is the organization MOST vulnerable to?
-
A. Rootkit
-
B. Worm
-
C. Logic bomb
-
D. Virus
Correct Wrong
-
-
Pytanie z
Which of the following BEST describes this malware?

-
A. Logic bomb
-
B. Trojan
-
C. Worm
-
D. Ransomware
Correct Wrong
Ransomware is a type of malware that encrypts a victim's files and demands payment, usually in cryptocurrency, in exchange for the decryption key. The behavior described in the question, such as encrypting files and demanding a ransom, aligns with the characteristics of ransomware.
-
-
Pytanie z
A web application firewall (WAF) is also known as a layer __ firewall
-
3
-
5
-
7
-
9
Correct Wrong
A web application firewall (WAF) is also known as a layer 7 firewall.
-
-
Pytanie z
A computer technician is configuring a firewall to allow certain traffic as follows: [..] Which of the following BEST describes this access control type?

-
A. Mandatory (MAC)
-
B. Rule-based
-
C. Discretionary (DAC)
-
D. Role-based
Correct Wrong
Wyjaśnienie Rule-based access control is a type of access control that enforces access restrictions based on rules defined by the system administrator. In the context of firewall configuration, rule-based access control involves setting up rules to allow or deny specific types of traffic based on criteria such as source IP address, destination IP address, port number, and protocol. This choice accurately describes the scenario where the technician is configuring the firewall to deny certain traffic based on rules.
-
-
Pytanie z
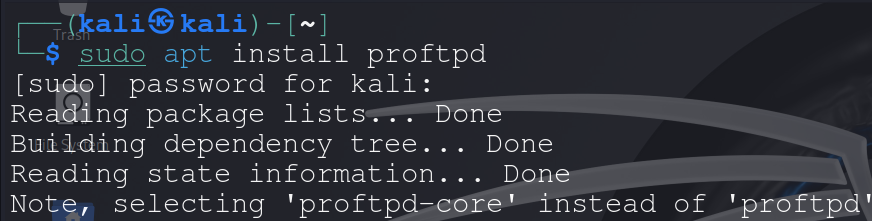
A penetration tester runs the following command at the terminal: Which of the following is MOST likely occurring?

-
A. Package monitoring
-
B. Vulnerability scan
-
C. SIEM logging
-
D. Malicious update
Correct Wrong
Package monitoring: Running the command "sudo apt install proftpd" installs the ProFTPD package on a Linux system. Package monitoring involves monitoring software packages for changes, updates, or vulnerabilities. In this context, by installing the ProFTPD package, the penetration tester could monitor its behaviour or vulnerabilities for security testing purposes.
-
-
Pytanie z
An organization received news that a vulnerability that had never been discovered previously has just been found, and they have to take all systems offline to prevent damage. Which of the following vulnerabilities is being described?
-
A. Improper patch management
-
B. Dark web
-
C. Zero-day
-
D. Lack of vendor support
Correct Wrong
-
-
Pytanie z
A disgruntled employee has left an organization. The employee sent an email announcing that at precisely 1 A.M., all files from the marketing department will be deleted. Which of the following attacks is being described?
-
A. Logic bomb
-
B. Impersonation
-
C. Pretexting
-
D. Ransomware
Correct Wrong
A logic bomb is a type of malicious code that is intentionally inserted into a system to execute a specific action at a predetermined time or when certain conditions are met. In this scenario, the disgruntled employee has set up a logic bomb to delete all files from the marketing department at a specific time, making this choice the correct answer.
-
-
Pytanie z
An organization is recovering from a ransomware infection that spread across the network. The security team is slowly bringing the systems back online. Which of the following incident response steps is the security team practicing?
-
A. Eradication
-
B. Lessons learned
-
C. Recovery
-
D. Identification
Correct Wrong
-
-
Pytanie z
A penetration tester is conducting an assessment against a well-known company and observes the following in a database file: Which of the following technologies is in use?

-
A. Tokenization
-
B. Hashing
-
C. Masking
-
D. Encryption
Correct Wrong
-
-
Pytanie z
A company plans to implement a new wireless network in their office building. A technician needs to determine the optimal placement of access points (APs) to ensure adequate Wi-Fi coverage. What is the MOST important step in this process?
-
A. Configuring the security settings on the wireless routers
-
B. Upgrading the internet bandwidth to support more devices
-
C. Conducting a site survey to assess the building layout and potential interference
-
D. Downloading a Wi-Fi analyzer app for employees to use
Correct Wrong
-
-
Pytanie z
A security analyst is investigating a series of failed login attempts on a critical server. The attacker is aware of some valid usernames but cannot guess the passwords. Which security controls would be most efficacious in mitigating this brute-force attack attempt?
-
A. Implementing a strong password policy with complex character requirements.
-
B. Enabling multi-factor authentication (MFA) for administrator accounts.
-
C. Increasing the password complexity requirements for all user accounts.
-
D. Configuring the server to lock out accounts after a specific number of failed login attempts.
Correct Wrong
Enabling multi-factor authentication (MFA) for administrator accounts is an effective security control to mitigate brute-force attacks. MFA adds an additional layer of security by requiring users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, making it harder for attackers to gain unauthorized access.
-
-
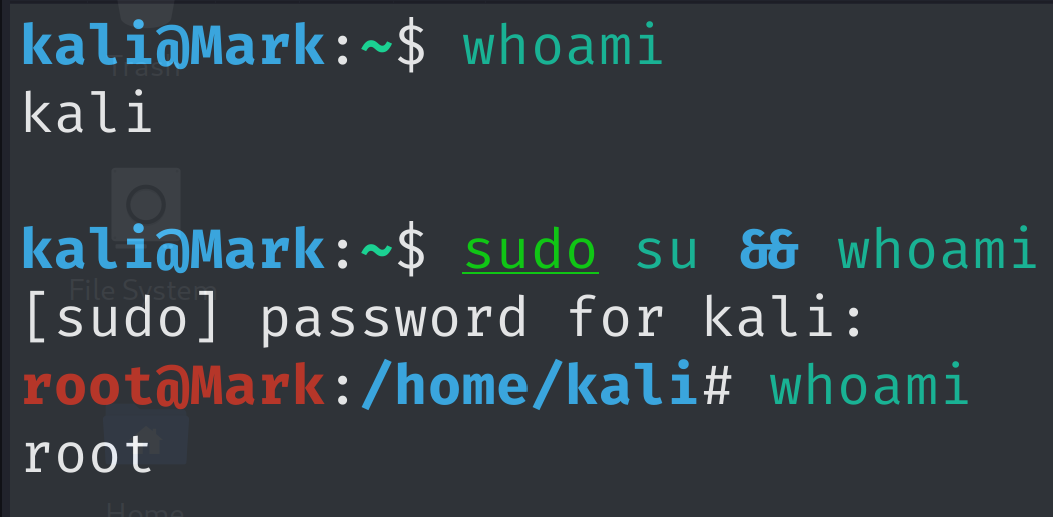
Pytanie z
An administrator runs a command and observes the following output: [..]Which of the following is being observed?

-
A. Malicious code
-
B. Cross-site scripting
-
C. TOCTOU
-
D. Privilege escalation
Correct Wrong
The observed output indicates privilege escalation. The command "sudo su" is used to switch to the root user, and the subsequent "whoami" command shows that the user has escalated privileges to the root user, which is a common indicator of privilege escalation.
-
-
Pytanie z
A security analyst discovers a zero-day exploit targeting a critical system within the network. There is no patch available yet from the vendor. What is the MOST appropriate initial action to take to mitigate the risk?
-
A. Update antivirus signatures on all endpoint devices.
-
B. Implement additional access controls for the system.
-
C. Increase the password complexity requirements for all user accounts.
-
D. Isolate the critical system from the network.
Correct Wrong
-
-
Pytanie z
A company is targeted by a phishing campaign where emails appear to be from a legitimate source, like the IT department. What type of social engineering attack is this MOST likely to be?
-
A. Smishing
-
B. Pretexting
-
C. Baiting
-
D. Tailgating
Correct Wrong
-
-
Pytanie z
A company recently experienced a data breach that leaked individuals’ usernames. An administrator reviews the logs of a web server and determines how the attacker accessed the resource. Which of the following attacks has took place?

-
A. SQL injection
-
B. Cross-site scripting
-
C. Pass the hash
-
D. Directory traversal
Correct Wrong
-
-
Pytanie z
A user is authenticating using a PIN and an RFID badge. The organization is looking to implement additional authentication factors beyond these factors. Which of the following additional authentication factors provides the BEST authentication?
-
A. Something you know
-
B. Somewhere you are
-
C. Something you have
-
D. Something you are
Correct Wrong
"Something you are" refers to biometric authentication factors such as fingerprint scans, facial recognition, or iris scans. Biometric authentication provides a high level of security as it is based on unique physical characteristics that are difficult to replicate or steal. This factor is considered the best authentication factor as it offers strong protection against unauthorized access.
-
-
Pytanie z
An organization’s blue team has deployed a system in hopes that the red team will reveal their techniques. Upon luring the opposing team, the solution captured attempted username and password logins. Which of the following technologies BEST describes this solution?
-
A. On-path attack
-
B. MITRE ATT&CK
-
C. Honeypot
-
D. DNS sinkhole
Correct Wrong
-
-
Pytanie z
After running a vulnerability scan against a system which is notorious for containing vulnerabilities, the penetration tester observes the following information:[…] Which of the following BEST describes this information?

-
A. False positive
-
B. CVSS
-
C. CVE
-
D. False negative
Correct Wrong
CVSS stands for Common Vulnerability Scoring System, which is a framework used to assess the severity of vulnerabilities based on various factors. The information provided by the penetration tester is likely related to the CVSS scores of the vulnerabilities found during the scan.
-
-
Pytanie z
An employee inside an organization has been silently gathering information for months on end. The employee received an email from a ransomware group stating that they would pay the employee large sums of money if the employee collected certain information. Which of the following is being described?
-
A. Unskilled attacker
-
B. Insider threat
-
C. APT
-
D. Organized crime
Correct Wrong
-
-
Pytanie z
An attacker is performing reconnaissance against a company using open-source tools. The attacker gathers information such as the company name, IP address, and email address. Which of the following is being described?
-
A. Scanning
-
B. Passive
-
C. Active
-
D. Penetration tester
Correct Wrong
Passive reconnaissance involves gathering information about a target without directly interacting with the target system or network. This type of reconnaissance is typically done using open-source tools and publicly available information, such as company name, IP address, and email address.
-
-
Pytanie z
A security administrator would like a way to segment a network from the rest of the organization. This separate network will be used solely for VoIP traffic. Which of the following would provide this functionality?
-
A. DMZ
-
B. Air-gap
-
C. Zero-trust
-
D. VLAN
Correct Wrong
VLAN (Virtual Local Area Network) is a method of creating separate logical networks within a physical network infrastructure. It allows for the segmentation of network traffic based on criteria such as department, function, or application. By creating a separate VLAN for VoIP traffic, the security administrator can effectively isolate and prioritize VoIP traffic within the organization's network.
-
-
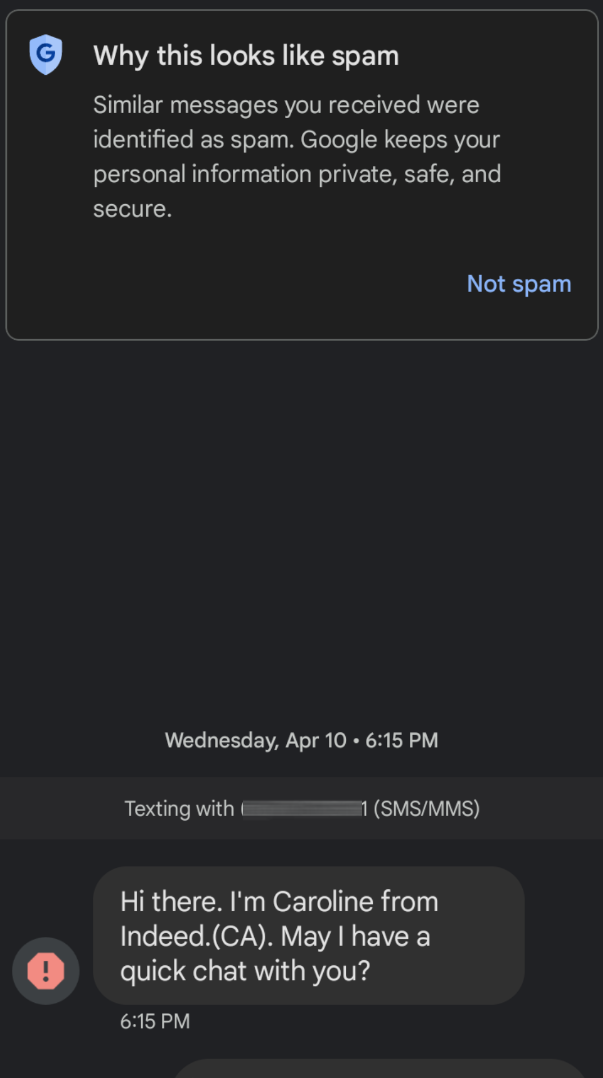
Pytanie z
A user has received the following message via SMS text:

-
A. File-based
-
B. Messaged-based
-
C. Image-based
-
D. Social engineering
Correct Wrong
Message-based threats usually refer to phishing or scam messages that attempt to deceive users into providing sensitive information. The primary focus of the question was on the fact that this threat is message-based.
-
-
Pytanie z
The „right to be forgotten” allows individuals to request:
-
A. Correction of inaccurate data
-
B. Deletion of their personal information
-
C. Access to their data for verification
-
D. Restriction of processing of their data
Correct Wrong
-
-
Pytanie z
A company implements a data inventory system to track all data assets. What is the MOST important benefit of maintaining an accurate data inventory?
-
A. Reducing storage costs by identifying and deleting unused data.
-
B. Simplifying software license management for various applications.
-
C. Enhancing the efficiency of data backup and recovery processes.
-
D. Identifying and mitigating security risks associated with sensitive data.
Correct Wrong
-
-
Pytanie z
You are configuring a new user account. Which principle of least privilege is MOST important to consider?
-
A. Grant users access to all resources they might need.
-
B. Assign users the minimum level of permissions required for their job function.
-
C. Allow users to share their credentials with colleagues.
-
D. Regularly review and update user access privileges.
Correct Wrong
Assigning users the minimum level of permissions required for their job function is the most important aspect of the principle of least privilege. This ensures that users only have access to the resources necessary to perform their specific tasks, limiting the potential damage that could occur in case of a security breach.
-
-
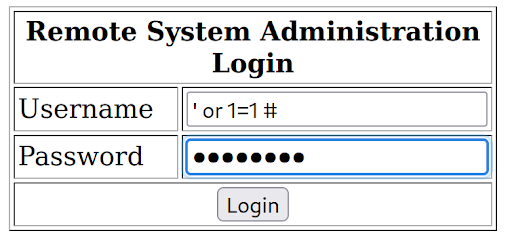
Pytanie z
A penetration tester observes the following login screen and performs an attack to bypass the login portal. Which of the subsequent attacks is being performed?

-
A. XSS
-
B. On-path
-
C. SQLi
-
D. Pass the hash
Correct Wrong
SQLi (SQL Injection) attacks involve inserting malicious SQL queries into input fields to manipulate the database backend of a web application. In this case, the penetration tester is likely exploiting a vulnerability in the login portal's database query to bypass the authentication process and gain unauthorized access.
-
-
Pytanie z
An administrator is adding randomization to hashed passwords, ensuring that identical pieces of information with different produce unique outputs. Which of the following is being described?
-
A. Salting
-
B. Hashing
-
C. Key stretching
-
D. IPSec
Correct Wrong
-
-
Pytanie z
An organization wants to secure a LAN/WLAN so users can authenticate and transport data securely. The solution needs to prevent on-path attacks and evil twin attacks. Which of the following will best meet the organization’s need?
-
A. MFA
-
B. 802.1X
-
C. WPA2
-
D. TACACS
Correct Wrong
-



GIPHY App Key not set. Please check settings