-
Pytanie z
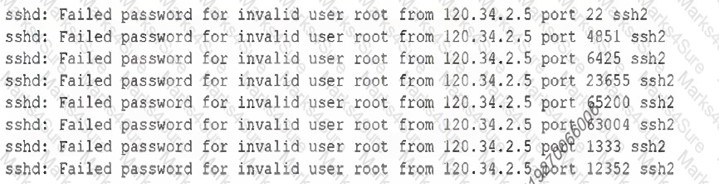
A security administrator checks the security logs of a Linux server and sees a lot of the following lines: [] Which of the following is most likely being attempted?

-
A. SQL injection attack
-
B. Rainbow table attack
-
C. Rootkit attack
-
D. Brute-force attack
Correct Wrong
-
-
Pytanie z
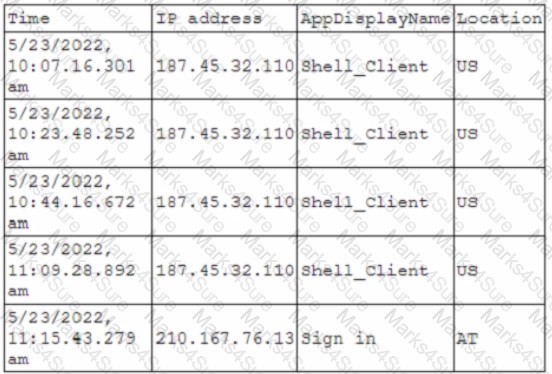
A security administrator received an alert for a user account with the following log activity:[]Which of the following best describes the trigger for the alert the administrator received?

-
A. Number of failed log-in attempts
-
B. Geolocation
-
C. Impossible travel time
-
D. Time-based log-in attempt
Correct Wrong
-
-
Pytanie z
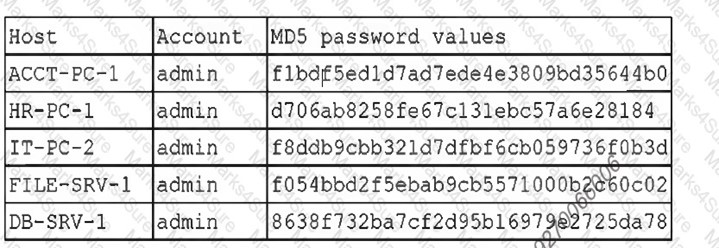
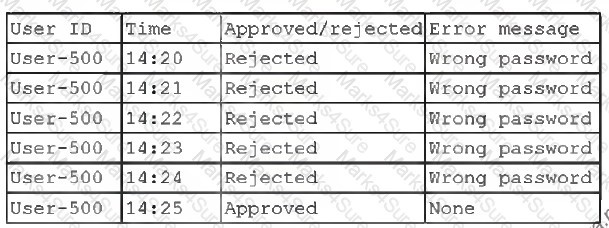
A security administrator recently reset local passwords and the2 following values were recorded in the system: [] Which of the following is the security administrator most likely protecting against?

-
A. Account sharing
-
B. Weak password complexity
-
C. Pass-the-hash attacks
-
D. Password compromise
Correct Wrong
-
-
Pytanie z
A prospective customer is interested in seeing the type of data that can be retrieved when a customer uses a company’s services. An engineer at the company sends the following documentation before reviewing it: [] The prospective customer is concerned. Which of the following will best resolve the concern?

-
A. Data sanitization
-
B. Software updates
-
C. Log aggregation
-
D. CASB
Correct Wrong
-
-
Pytanie z
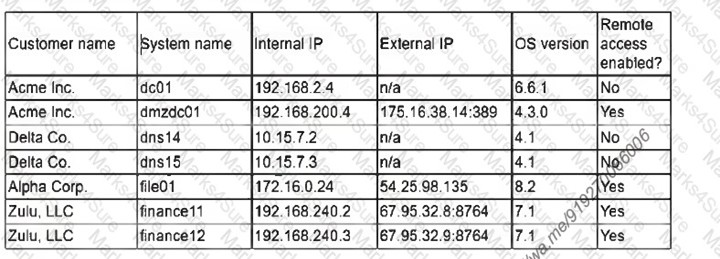
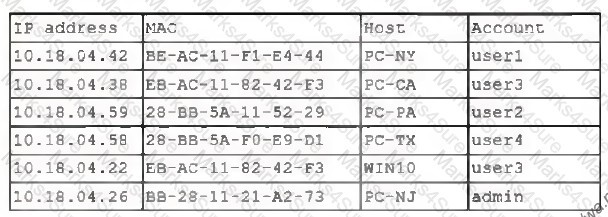
A security analyst finds a rogue device during a monthly audit of current endpoint assets that are connected to the network. The corporate network utilizes 802.1X for access control. To be allowed on the network, a device must have a known hardware address, and a valid username and password must be entered in a captive portal. The following is the audit report:[]Which of the following is the most likely way a rogue device was allowed to connect?

-
A. A user performed a MAC cloning attack with a personal device.
-
B. A DHCP failure caused an incorrect IP address to be distributed.
-
C. An administrator bypassed the security controls for testing.
-
D. DNS hijacking let an attacker intercept the captive portal traffic.
Correct Wrong
-
-
Pytanie z
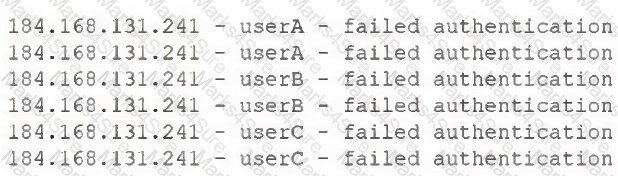
The security operations center is researching an event concerning a suspicious IP address. A security analyst looks at the following event logs and discovers that a significant portion of the user accounts have experienced failed log-in attempts when authenticating event logs and discovers that a significant portion of the user accounts have experienced failed log-in attempts when authenticating from the same IP address:[]Which of the following most likely describes the attack that took place?

-
A. Spraying
-
B. Brute-force
-
C. Dictionary
-
D. Rainbow table
Correct Wrong
-
-
Pytanie z
A security analyst finds that a user’s name appears in a database entry at a time when the user was on vacation. The security analyst reviews the following logs from the authentication server that is being used by the database:[] Which of the following can the security analyst conclude based on the review?

-
A. A brute-force attack occurred.
-
B. A rainbow table uncovered the password.
-
C. Technical controls did not block the reuse of a password.
-
D. An attacker used password spraying.
Correct Wrong
-
-
Pytanie z
A security analyst is investigating a SIEM event concerning invalid log-ins The system logs that match the time frame of the event show the following:[] Which of the following best describes this type of attack?

-
A. Rainbow table
-
B. Spraying
-
C. Dictionary
-
D. Keylogger
Correct Wrong
-
-
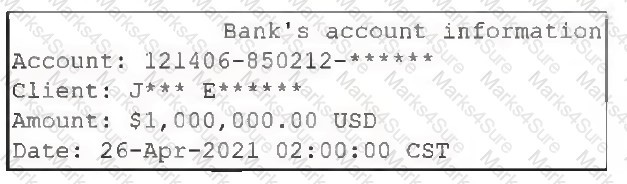
Pytanie z
A web application for a bank displays the following output when showing details about a customer’s bank account:[]Which of the following techniques is most likely implemented in this web application?

-
A. Data minimization
-
B. Data scrambling
-
C. Data masking
-
D. Anonymization
Correct Wrong
-
-
Pytanie z
An administrator receives the following network requirements for a data integration with a third-party vendor: [] Which of the following is the most appropriate response for the administrator to send?

-
A. FTP is an insecure protocol and should not be used.
-
B. Port 8080 is a non-standard port and should be blocked.
-
C. SSH protocol version 1 is obsolete and should not be used.
-
D. Certificate stapling on port 443 is a security risk that should be mitigated
Correct Wrong
-
-
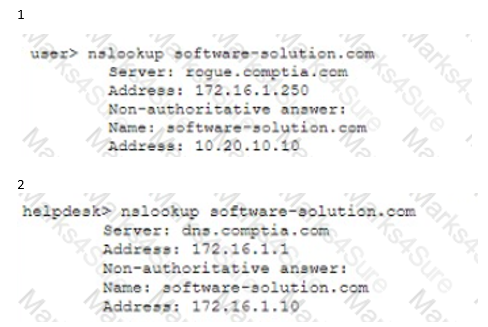
Pytanie z
A user attempts to load a web-based application, but the expected login screen does not appear A help desk analyst troubleshoots the issue by running the following command and reviewing the output on the user’s PC
[1]
The help desk analyst then runs the same command on the local PC
[2]
-
A. Domain hijacking
-
B. DNS poisoning
-
C. MAC flooding
-
D. Evil twin
Correct Wrong
-
-
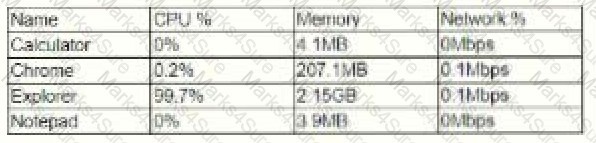
Pytanie z
A user reports trouble using a corporate laptop. The laptop freezes and responds slowly when writing documents and the mouse pointer occasional disappears. The task list shows the following results [] Which of the following is MOST likely the issue?

-
A. RAT
-
B. PUP
-
C. Spyware
-
D. Keylogger
Correct Wrong
-
-
Pytanie z
The following are the logs of a successful attack. [] Which of the following controls would be BEST to use to prevent such a breach in the future?

-
A. Password history
-
B. Account expiration
-
C. Password complexity
-
D. Account lockout
Correct Wrong
-
-
Pytanie z
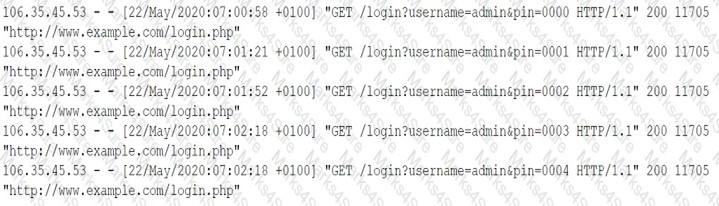
A security analyst is investigating what appears to be unauthorized access to a corporate web application. The security analyst reviews the web server logs and finds the following entries: [] Which of the following password attacks is taking place?

-
A. Dictionary
-
B. Brute-force
-
C. Rainbow table
-
D. Spraying
Correct Wrong
-
-
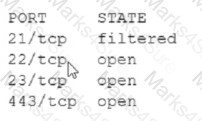
Pytanie z
An analyst Is generating a security report for the management team. Security guidelines recommend disabling all listening unencrypted services. Given this output from Nmap: [] Which of the following should the analyst recommend to disable?

-
A. 21/tcp
-
B. 22/tcp
-
C. 23/tcp
-
D. 443/tcp
Correct Wrong
A. 21/tcp – ftp nieszyfrowane B. 22/tcp - -SFTP C. 23/tcp - telnet D. 443/tcp
-
-
Pytanie z
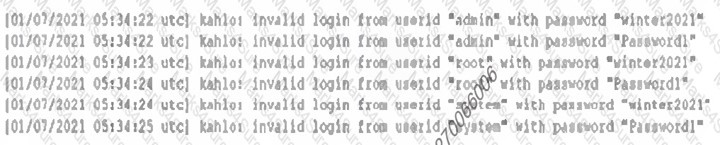
A company was compromised, and a security analyst discovered the attacker was able to get access to a service account. The following logs were discovered during the investigation: [] Which of the following MOST likely would have prevented the attacker from learning the service account name?

-
A. Race condition testing
-
B. Proper error handling
-
C. Forward web server logs to a SIEM
-
D. Input sanitization
Correct Wrong
-
-
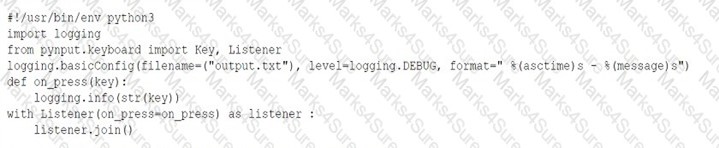
Pytanie z
Given the following snippet of Python code: [] Which of the following types of malware MOST likely contains this snippet?

-
A. Logic bomb
-
B. Keylogger
-
C. Backdoor
-
D. Ransomware
Correct Wrong
-
-
Pytanie z
A user reports constant lag and performance issues with the wireless network when working at a local coffee shop A security analyst walks the user through an installation of Wireshark and gets a five-minute pcap to analyze. The analyst observes the following output: [] Which of the following attacks does the analyst most likely see in this packet capture?

-
A. Session replay
-
B. Evil twin
-
C. Bluejacking
-
D. ARP poisoning
Correct Wrong
-
-
Pytanie z
During a forensic investigation, a security analyst discovered that the following command was run on a compromised host: [] Which of the following attacks occurred?

-
A. Buffer overflow
-
B. Pass the hash
-
C. SQL injection
-
D. Replay attack
Correct Wrong
-
-
Pytanie z
A customer has reported that an organization’s website displayed an image of a smiley (ace rather than the expected web page for a short time two days earlier. A security analyst reviews log tries and sees the following around the lime of the incident: [] Which of the following is MOST likely occurring?

-
A. Invalid trust chain
-
B. Domain hijacking
-
C. DNS poisoning
-
D. URL redirection
Correct Wrong
-
-
Pytanie z
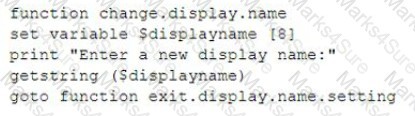
While performing a threat-hunting exercise, a security analyst sees some unusual behavior occurring in an application when a user changes the display name. The security analyst decides to perform a static code analysis and receives the following pseudocode: [] Which of the following attack types best describes the root cause of the unusual behavior?

-
A. Server-side request forgery
-
B. Improper error handling
-
C. Buffer overflow
-
D. SQL injection
Correct Wrong
-
-
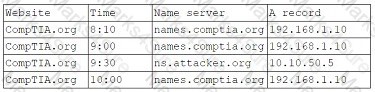
Pytanie z
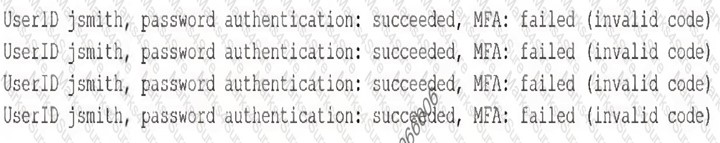
A security analyst reviews domain activity logs and notices the following: [] Which of the following is the best explanation for what the security analyst has discovered?

-
A. The user jsmith’s account has been locked out.
-
B. A keylogger is installed on jsmith’s workstation.
-
C. An attacker is attempting to brute force jsmith’s account.
-
D. Ransomware has been deployed in the domain.
Correct Wrong
-
-
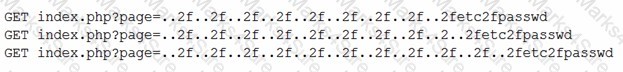
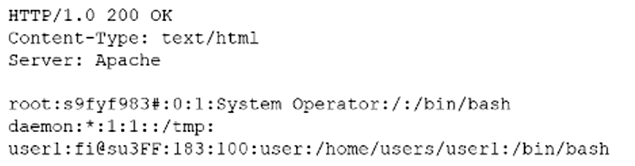
Pytanie z
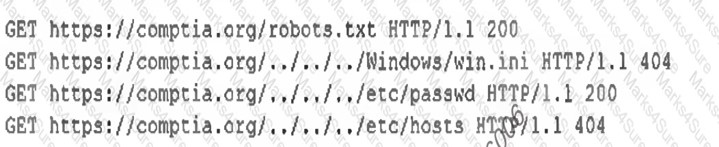
An analyst examines the web server logs after a compromise and finds the following: [] Which of the following most likely indicates a successful attack on server credentials?

-
A. GET https://comptia.org/robots.txt HTTP/1.1 200
-
B. GET https://comptia.org/../../../Windows/win.ini HTTP/1.1 404
-
C. GET HTTP/1.1 200 https://comptia.org/../../../etc/passwd
-
D. GET https://comptia.org/./…/../etc/hosts HTTP/1.1 404
Correct Wrong
-
-
Pytanie z
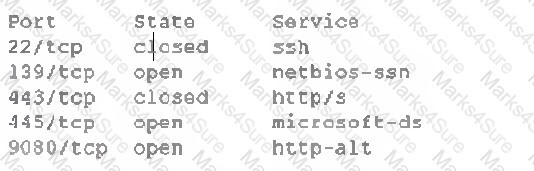
A system administrator performs a quick scan of an organization’s domain controller and finds the following: [] Which of the following vulnerabilities does this output represent?

-
A. Unnecessary open ports
-
B. Insecure protocols
-
C. Misconfigured firewall
-
D. Weak user permissions
Correct Wrong
-
-
Pytanie z
A security analyst is reviewing an IDS alert and sees the following:
C:WindowsSystem32WindowsPowershellv1.0powershell.exe -noP -exe byPass -nonI -wind hidden -no1 -c dir;findstr /s maldinuv %USERPROFILE%\*.lnk > %USERPROFILE%Documentsiijlqe.ps1;%USERPROFILE%Documentsiijlqe.psi;exit
[]
Which of the following triggered the IDS alert?
-
A. MAC flooding
-
B. URL redirection
-
C. ARP poisoning
-
D. DNS hijacking
Correct Wrong
-
-
Pytanie z
A network analyst is investigating compromised corporate information. The analyst leads to a theory that network traffic was intercepted before being transmitted to the internet. The following output was captured on an internal host: [] Based on the IoCS, which of the following was the MOST likely attack used to compromise the

-
A. Denial of service
-
B. ARP poisoning
-
C. Command injection
-
D. MAC flooding
Correct Wrong
-
-
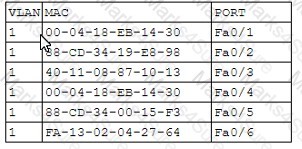
Pytanie z
A network engineer receives a call regarding multiple LAN-connected devices that are on the same switch. The devices have suddenly been experiencing speed and latency issues while connecting to network resources. The engineer enters the command show mac address-table and reviews the following output. [] Which of the following best describes the attack that is currently in progress?

-
A. MAC flooding
-
B. Evil twin
-
C. ARP poisoning
-
D. DHCP spoofing
Correct Wrong
-
-
Pytanie z
A security analyst is investigating network issues between a workstation and a company server. The workstation and server occasionally experience service disruptions, and employees are forced to reconnect to the server. In addition, some reports indicate sensitive information is being leaked from the server to the public. The workstation IP address is 192.168.1.103, and the server IP address is 192.168.1.101. The analyst runs arp -a On a separate workstation and obtains the following results: [] Which of the following is most likely occurring?

-
A. Evil twin attack
-
B. Domain hijacking attack
-
C. On-path attack
-
D. MAC flooding attack
Correct Wrong
-
-
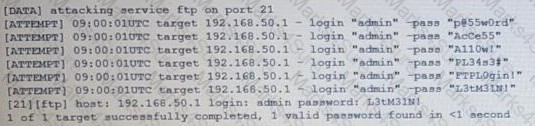
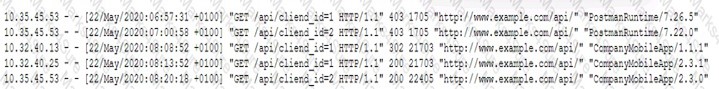
Pytanie z
A security analyst is investigating a report from a penetration test. During the penetration test, consultants were able to download sensitive data from a back-end server. The back-end server was exposing an API that should have only been available from the compans mobile application. After reviewing the back-end server logs, the security analyst finds the following entries [] Which of the following is the most likely cause of the security control bypass?

-
A. IP address allow list
-
B. user-agent spoofing
-
C. WAF bypass
-
D. Referrer manipulation
Correct Wrong
-
-
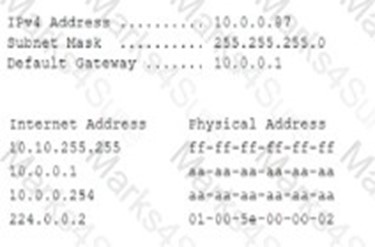
Pytanie z
A security administrator examines the ARP table of an access switch and sees the following output: [] Which of the following is a potential threat that is occurring on this access switch?

-
A. DDoS on Fa02 port
-
B. MAC flooding on Fa0/2 port
-
C. ARP poisoning on Fa0/1 port
-
D. DNS poisoning on port Fa0/1
Correct Wrong
-
-
Pytanie z
A security engineer obtained the following output from a threat intelligence source that recently performed an attack on the company’s server: [] Which of the following best describes this kind of attack?

-
A. Directory traversal
-
B. SQL injection
-
C. API
-
D. Request forgery
Correct Wrong
-
-
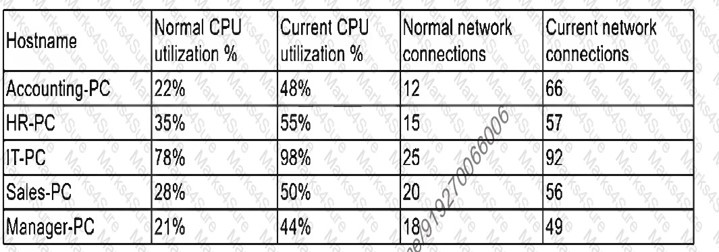
Pytanie z
Several users have opened tickets with the help desk. The help desk has reassigned the tickets to a security analyst for further review. The security analyst reviews the following metrics: [] Which of the following is most likely the result of the security analyst’s review?

-
A. The ISP is dropping outbound connections.
-
B. The user of the Sales-PC fell for a phishing attack.
-
C. Corporate PCs have been turned into a botnet.
-
D. An on-path attack is taking place between PCs and the router.1
Correct Wrong
-
-
Pytanie z
A security analyst is reviewing logs on a server and observes the following output: [] Which of the following is the security analyst observing?

-
A. A rainbow table attack
-
B. A password-spraying attack
-
C. A dictionary attack
-
D. A keylogger attack
Correct Wrong
-
-
Pytanie z
A security analyst it investigating an incident to determine what an attacker was able to do on a compromised Laptop. The analyst reviews the following SIEM log: [] Which of the following describes the method that was used to compromise the laptop?

-
A. An attacker was able to move laterally from PC 1 to PC2 using a pass-the-hash attach
-
B. An attacker was able to bypass the application approve list by emailing a spreadsheet. attachment with an embedded PowerShell in the file.
-
C. An attacker was able to install malware to the CAasdf234 folder and use it to gain administrator rights and launch Outlook
-
D. An attacker was able to phish user credentials successfully from an Outlook user profile
Correct Wrong
-
-
Pytanie z
A security analyst is reviewing SIEM logs during an ongoing attack and notices the following: [] Which of the following best describes the type of attack?

-
A. SQLi
-
B. CSRF
-
C. API attacks
-
D. Directory traversal
Correct Wrong
-
-
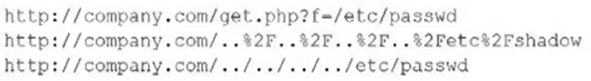
Pytanie z
A secondly administration is trying to determine whether a server is vulnerable to a range of attacks After using a tool, the administrator obtains the following output. [] Which of the following attacks was successfully implemented based on the output?

-
A. Memory leak
-
B. Race condition
-
C. SQL injection
-
D. Directory traversal
Correct Wrong
-
-
Pytanie z
Security analysts are conducting an investigation of an attack that occurred inside the organization’s network. An attacker was able to coiled network traffic between workstations throughout the network The analysts review the following logs: The Layer 2 address table has hundreds of entries similar to the ones above. [] Which of the following attacks has most likely occurred?

-
A. SQL injection
-
B. DNS spoofing
-
C. MAC flooding
-
D. ARP poisoning
Correct Wrong
-
-
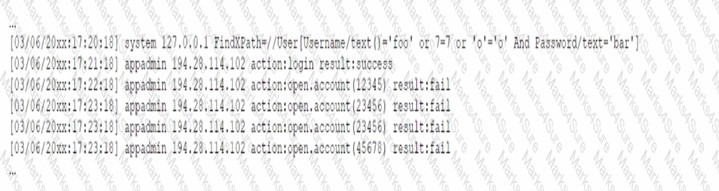
Pytanie z
A security analyst receives a SIEM alert that someone logged in to the app admin test account, which is only used for the early detection of attacks. The security analyst then reviews the following application log: [] Which of the following can the security analyst conclude?

-
A. A replay attack is being conducted against the application.
-
B. An injection attack is being conducted against a user authentication system.
-
C. A service account password may have been changed, resulting in continuous failed logins within the application.
-
D. A credentialed vulnerability scanner attack is testing several CVEs against the application.
Correct Wrong
-
-
Pytanie z
An organization received threat intelligence describing an increase in credential harvesting across the industry A security analyst is reviewing the following authentication logs to look for potential Indicators of compromise. Which of the following configurations can help prevent this hype of attack from occurring?

-
A. Blocking malicious IPs
-
B. Enabling impossible logins
-
C. Deploying privileged access management
-
D. Setting the max account lockout threshold
Correct Wrong
-













GIPHY App Key not set. Please check settings